Adversarial Attack Demo

Adversarial attacks! Engineer images to fool/attack Neural Networks | Self driving cars get confusedПодробнее

[PLDI'23] One Pixel Adversarial Attacks via Sketched ProgramsПодробнее
![[PLDI'23] One Pixel Adversarial Attacks via Sketched Programs](https://img.youtube.com/vi/kc38ZvXU5Wg/0.jpg)
Five examples of adversarial machine learning attacksПодробнее

Adversarial attack in AI| How Adversarial attack misguides? Solution about Adversarial attack?Подробнее

Erosion Attack Harnessing Corruption To Improve Adversarial ExamplesПодробнее

Evolutionary Multilabel Adversarial Examples An Effective Black Box AttackПодробнее

VehicleSec 2024 - Demo: CARLA-based Adversarial Attack Assessment on Autonomous VehiclesПодробнее

NDSS 2024 - Parrot-Trained Adversarial Examples: Pushing the Practicality of Black-Box Audio AttacksПодробнее

NECST Friday Talk @ 20240517 - Stealthy Adversarial Examples in Computer Vision ModelsПодробнее

NDSS 2024 - Enhance Stealthiness and Transferability of Adversarial Attacks with Class Activation MaПодробнее

USENIX Security '23 - KENKU: Towards Efficient and Stealthy Black-box Adversarial Attacks against...Подробнее

Scattering Model Guided Adversarial Examples for SAR Target Recognition Attack and DefenseПодробнее

[Demo] MAP: Multispectral Adversarial Patch to Attack Person DetectionПодробнее
![[Demo] MAP: Multispectral Adversarial Patch to Attack Person Detection](https://img.youtube.com/vi/TEXsCBQf3ek/0.jpg)
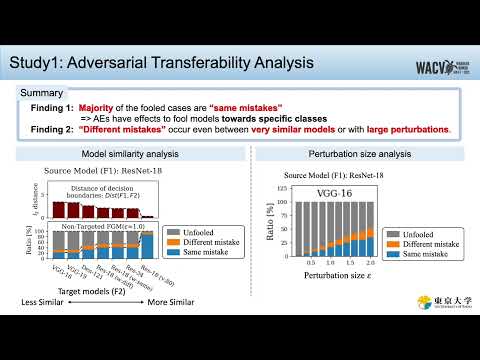
Closer Look at the Transferability of Adversarial Examples: How They Fool Different Models DifferenПодробнее
[Demo]Defending Physical Adversarial Attack on Object Detection via Adversarial Patch-Feature EnergyПодробнее
![[Demo]Defending Physical Adversarial Attack on Object Detection via Adversarial Patch-Feature Energy](https://img.youtube.com/vi/truU_rY0I3s/0.jpg)
Evolutionary Multilabel Adversarial Examples An Effective Black Box AttackПодробнее

Multi Spectral Palmprints Joint Attack and Defense With Adversarial Examples LearningПодробнее

Universal and Transferable Adversarial Attacks on Aligned Language Models ExplainedПодробнее

Lecture 4 - Deep Neural Networks and Adversarial ExamplesПодробнее
