Analyzing Windows Malware on Linux: Getting Started Tips and Examples

Crash Course: Linux Log Analysis | Beginner Guide for SOC Analyst | Security InvestigationПодробнее
Discover The Power Of Microsoft 365 Defender: Your Guide To Getting Started | Peter Rising MVPПодробнее

How Do You Handle Malware Safely? Start By Learning the REMnux VM!Подробнее

Disk Analysis with Autopsy | HackerSploit Blue Team TrainingПодробнее
Linux vs Windows: MalwareПодробнее
Cybersecurity Tool: Malware Virtual Machines (Remnux & FlareVM)Подробнее

ESET: Linux Malware Hunter Reveals His TipsПодробнее
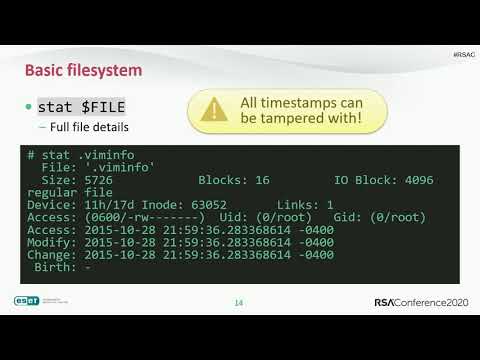
Quick Look: Analyzing Windows Malware on Linux: Getting Started Tips and ExamplesПодробнее

MALWARE ANALYSIS // How to get started with John HammondПодробнее
Getting Started With Ghidra For Malware AnalysisПодробнее

What’s New in REMnux v7Подробнее
