Bettercap tutorial | #part-1 | ARP spoofing | MITM attack | Ethical Hacking

Bettercap tutorial | #part-2 | DNS poisoning | MITM attack | Ethical HackingПодробнее

Home Lab 14: ARP & DNS Spoofing with BettercapПодробнее

hacking every device on local networks - bettercap tutorial (Linux)Подробнее

105 Подмена ARP BettercapПодробнее

MITM Attack using ARP Spoofing & BettercapПодробнее

MiTM Attack | ARP Spoofing | ARP Poisoning in Kali LinuxПодробнее

Get Usernames and Passwords with Ettercap, ARP Poisoning (Cybersecurity)Подробнее
Bettercap ARP Spoofing🕵🏼Man In The Middle - MITM 15.2Подробнее
Intercept and modify network traffic EASY MITM Attack (Bettercap tutorial)Подробнее

ARP SPOOFING using bettercap in Kali Linux | ARP Spoofing and Sniffing using bettercap in Kali LinuxПодробнее

How to do ARP Spoofing with BettercapПодробнее

Hacking ARP: Hands-On Attack Using Bettercap for Advanced Network ExploitationПодробнее

MITM With Ettercap - ARP PoisoningПодробнее

HOW TO USE BETTERCAP FOR ARP SPOOFINGПодробнее

KALI LINUX #8 MITM ATTACK #1 USING BETTERCAPПодробнее

Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoCПодробнее

how Hackers SNiFF (capture) network traffic // MiTM attackПодробнее

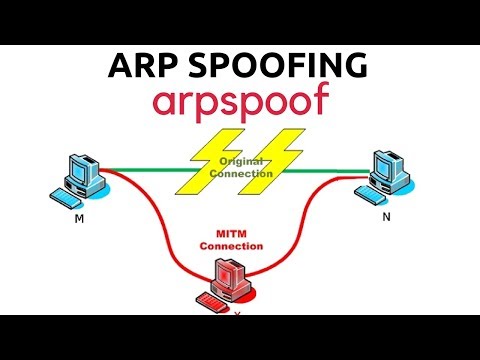
ARP Spoofing With arpspoof - MITMПодробнее