Bug Bounty Guide for Beginners
XSS Methodology for Bug Bounty Hunters #xsspoc2025 #bugbountypocxssПодробнее

How to Find XSS on Modern Web Applications: A Bug Bounty GuideПодробнее

XSS Methodology for Bug Bounty Hunters | WordPress GuideПодробнее
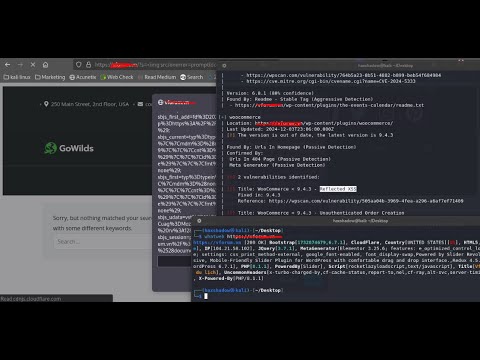
Proven XSS Methodology for Bug Bounty Hunters | WordPress GuideПодробнее
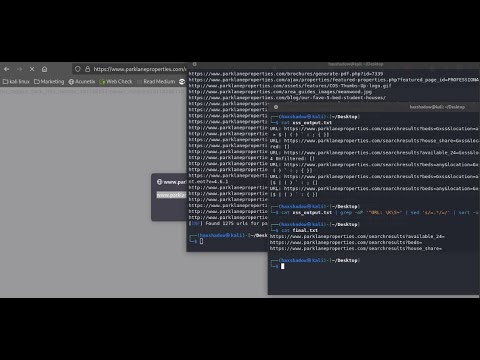
Bug Bounty Basics: A Beginner's Guide to Ethical HackingПодробнее

SQL Injection Bounty | Bug bounty POC |SQL Injection Vulnerability - PoC| SQLi Vulnerability 2024Подробнее
What is a Web3 CTF? Beginner's Guide to Excelling in Blockchain Security ChallengesПодробнее

CBBH Exam Guide: Certified Bug Bounty Hunter Review & Tips | HackTheBoxПодробнее

How to Get Your First Bug Bounty Payout Quickly | Beginner's Guide to Web3 Bug BountiesПодробнее

What Is Cross-Site Scripting (XSS)? | Bug Bounty Hunting Guide to an Advanced Earning MethodПодробнее

LFI and XSS Vulnerabilities Explained | Bug Bounty Hunting Made EasyПодробнее
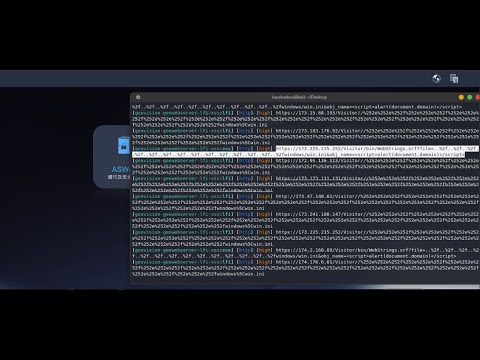
Live Bughunting For Beginner - Sublister - GuideПодробнее

Tools for Bug Bounty || Instagram hack || Instagram Ethical Hacking || how to hack Instagram!Подробнее

How to Learn Bug Bounty Hunting (for Beginners) - a Comprehensive GuideПодробнее
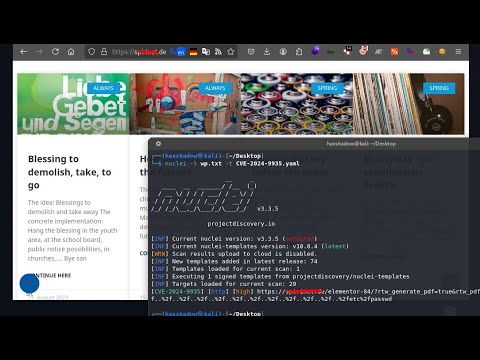
Easy way to Find LFI cve+manually+Automation | Bug bounty pocПодробнее
Virtual Box and Kali Linux Download | Ultimate Bug Bounty & Web Application Security Course (Part 3)Подробнее

Master Nmap Basics | Bug Bounty & Web Security Course (Part 13)Подробнее

Beginner's Guide to Response Manipulation in Bug Bounty ProgramsПодробнее

Bug Bounty Hunting: Asset-finder Installation & Usage in Hindi | Complete GuideПодробнее

Tesla Subdomain Hunting: A Bug Bounty Researcher’s Guide 🔥 #tesla #ethicalhacking #bugbountyПодробнее
