Cilium Kubernetes CNI Provider, Part 1: Overview of eBPF and Cilium and the Installation Process
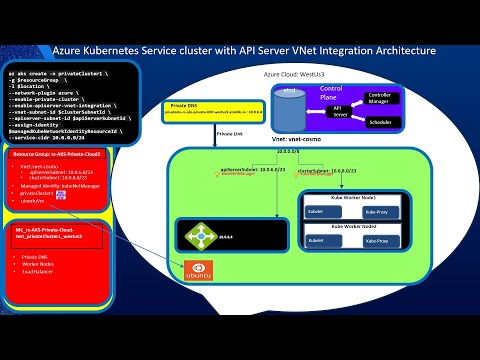
Setup Azure Kubernetes Private Clusters with API Server Vnet IntegrationПодробнее
Istio and Cilium: Pushing the Boundaries of the Possible on Zero-Trust - Lin Sun, Solo.ioПодробнее

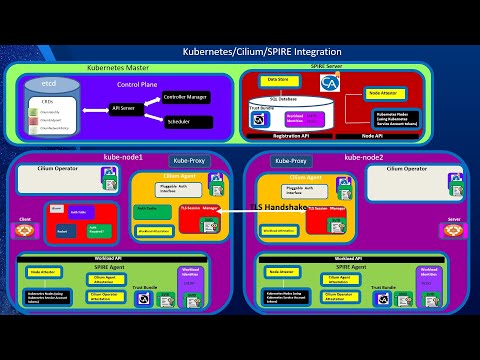
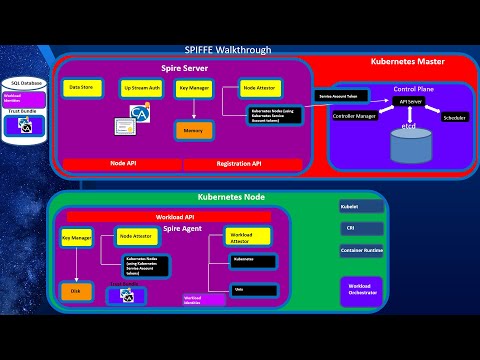
Workload Identity Part 2: How Cilium Implements Its Mutual Auth Leveraging SPIFFE and SPIREПодробнее
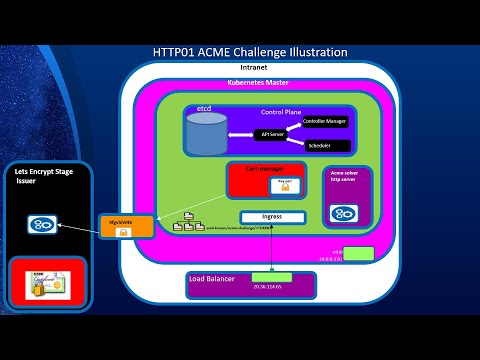
Encrypt Client Communication to Kubernetes Services Leveraging Cert-Manage and Let’s EncryptПодробнее
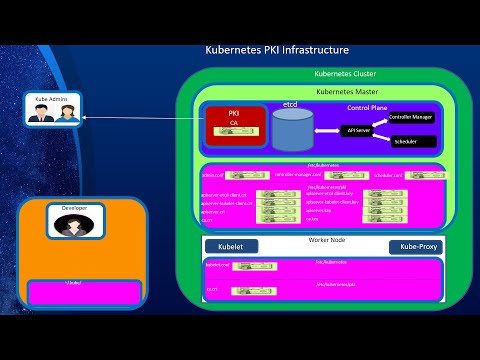
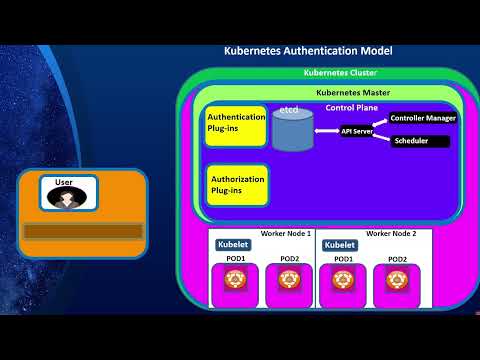
Kubernetes Security, Part 3: Kubernetes Auth (Part A: Overview and X509 Client Certificate auth)Подробнее
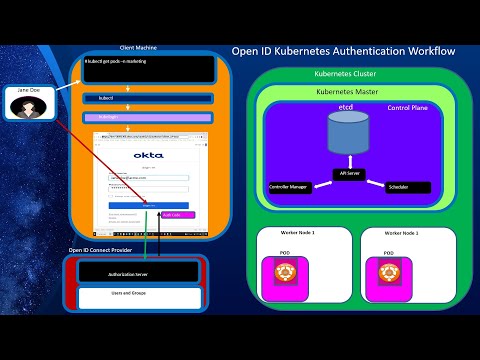
Kubernetes Security, Part 4: Kubernetes Authentication (Part B: Open ID Connect Auth)Подробнее
Kubernetes networking and Cilium - Part 1Подробнее

Workload Identity Part 1: Introduction to SPIFFE and SPIREПодробнее
Cilium’s Evolution: The Founding Story of CiliumПодробнее

From Zero to Cluster Mesh: Installing and Configuring Cilium CNI on KubernetesПодробнее

Cilium Service MeshПодробнее

Cilium Kubernetes CNI Provider: Part 4, IP Routing Modes (Direct and Encapsulated)Подробнее

Kubernetes Security, Part 1: Kubernetes Security Overview and Role Based Access Control (RBAC)Подробнее
Cilium Kubernetes CNI Provider, Part 3: Cluster MeshПодробнее

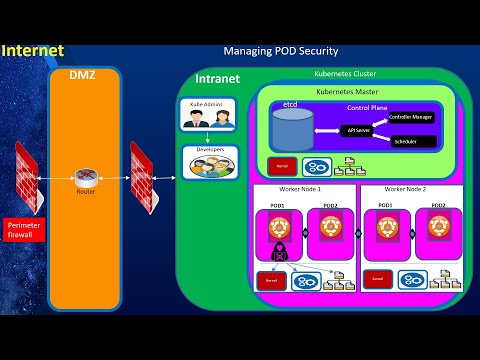
Kubernetes Security, Part 2: Managing POD Run Time SecurityПодробнее
Cilium Kubernetes CNI Provider, Part 2: Security Policies and Observability Leveraging HubbleПодробнее
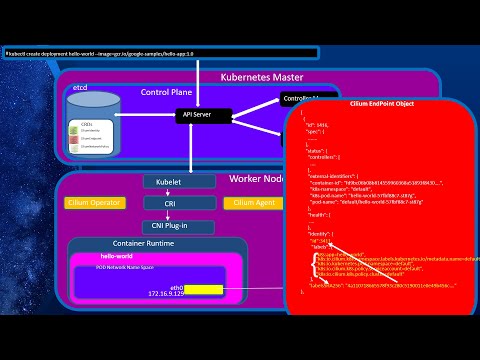
Cilium Service Mesh on AWS EKS | Part 1Подробнее
Istio Ambient Service MeshПодробнее
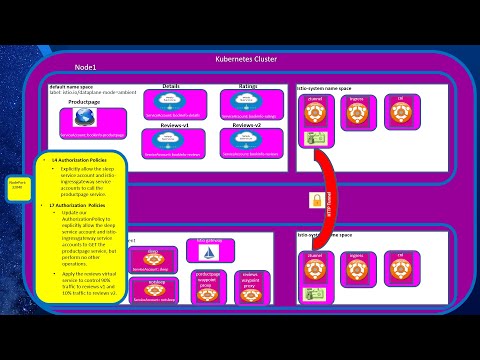
Pimp your Kubernetes cluster with Cilium, e-BPF based Networking and ObservabilityПодробнее

Cilium: Welcome, Vision and Updates - Thomas Graf & Liz Rice, Isovalent; Laurent Bernaille, DatadogПодробнее
