Cloud OnAir: How Secure Are Your APIs?

Cloud OnAir: How to protect your APIs from security vulnerabilities leveraging OWASP best practicesПодробнее

How Secure Are Your APIs?Подробнее

How secure are your APIs?Подробнее

How secure are your APIs?Подробнее

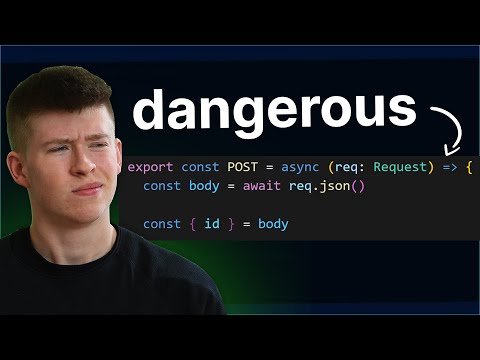
How to ACTUALLY Secure Your API (5 Steps)Подробнее
Cloud OnAir: How to Connect Modern APIs with Existing Identity Management SystemsПодробнее

How to protect your APIs against these 6 security threatsПодробнее

How Secure are Your APIs? (Cloud Next '18)Подробнее

OWASP best practices to protect your APIs from security vulnerabilitiesПодробнее

This is the best way to protect your APIsПодробнее

Cloud OnAir: Build modern apps using an API-First strategyПодробнее

Protect your web apps and APIs against threats and fraud with Google CloudПодробнее

Best practices for securing your APIs & ApplicationsПодробнее

Cloud OnAir: Unravel the mystery of container securityПодробнее

Cloud OnAir: Why APIs are products not one-off projectsПодробнее

Understanding The Fundamentals of API Security | How APIs are Attacked and How to Secure ThemПодробнее

OAuth, JWT, HMAC, oh my! API security for your enterpriseПодробнее
