Creating a Network Access Policy
Manage Network Access with NetBirdПодробнее

Network access management with NACVIEW and 802.1x.Подробнее

Forget AWS VPN, start using Zero-Trust Network AccessПодробнее

Introducing Microsoft Global Secure Access - No More VPN's!Подробнее

Fortinet Full Stack: Configuring FortiGate, FortiSwitch, FortiAP | SD-WAN, VLAN, SSID, w/FortiLink!Подробнее

Applying Zero Trust Based Network Access to access internal Applications | Entra Private AccessПодробнее

FortiGate Zero Trust Network Access (ZTNA) Lab for On-Network or Internal UsersПодробнее

How to Configure Zero Trust Remote Access to a Single NetworkПодробнее

Launching your first vector engine on Amazon OpenSearch Serverless | Amazon Web ServicesПодробнее

Install a self-hosted VPN platform // NetbirdПодробнее

Microsoft Entra Private Access Step by Step Tutorial and Demo using Zero TrustПодробнее

STOP using VPN, embrace Zero-Trust networking!Подробнее

FortiNAC Demo | Fortinet's Network Access Control SolutionПодробнее

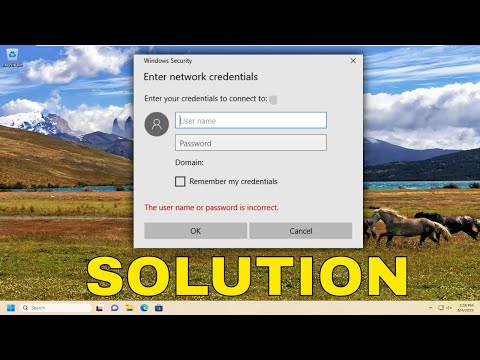
Fix Enter Network Credentials Error on Windows 11/10 (Guide)Подробнее
Jamf Connect – Identity and Zero Trust Network Access | JNUC 2023Подробнее

OPNsense Firewall Rule OrderПодробнее

Understanding Network Access Control Lists (NACLs) and Configuring SSH Blocking Rules||network aclПодробнее

Introduction to Microsoft’s Security Service Edge for Identity-Centric Network AccessПодробнее

Live: External Network Access on Snowpark (PuPr)Подробнее

Safeguard your wired network access with user and machine authentication and authorizationПодробнее
