DEFCON 15: Stealing Identity Management Systems

DEF CON 25 - Lee Holmes - Get $pwnd: Attacking Battle Hardened Windows ServerПодробнее

DEF CON 15 Hacking Conference Presentation By Plet - Stealing Identity Management Systems - VideoПодробнее

DEF CON 15 - Greg Hoglund - Virtual World Real HackingПодробнее
DEFCON 15: Saving The Internet With HateПодробнее

Cybersecurity Expert Demonstrates How Hackers Easily Gain Access To Sensitive InformationПодробнее

DEFCON 16: Medical Identity TheftПодробнее

DefCon 15 T538 Stealing IdentityПодробнее

DEF CON 15 - Plet - Stealing Identity Management SystemsПодробнее

DEFCON 15: VIRTUAL WORLD, REAL HACKINGПодробнее
Kiosk mode Bruteforce Evasion with Flipper ZeroПодробнее
DEF CON 15 - Phillip Zimmerman - Z PhoneПодробнее

DEF CON 15 - Robert Clark - Computer and Internet Security LawПодробнее
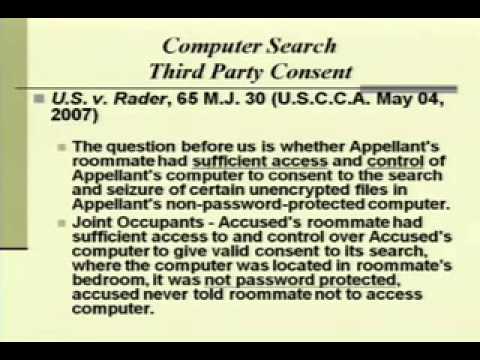
How Law Enforcement Breaks into iPhonesПодробнее

DEFCON 19: Steal Everything, Kill Everyone, Cause Total Financial Ruin! (w speaker)Подробнее

Hacking challenge at DEFCONПодробнее

DEF CON 16 - Eric Smith & Dr. Shana Dardan: Medical Identity TheftПодробнее

DEFCON 15: Greater than 1: Defeating "strong" Authentication in Web ApplicationsПодробнее

DEFCON 14: Your Name, Your Shoe Size, Your Identity? What do we Trust in this Web?Подробнее

DEF CON 15 - Bruce Potter - Dirty Secrets of the Security industryПодробнее
