Defending Against Buffer Overflow Attacks: Expert Insights #cybersecurity #bufferoverflow

Атака переполнения буфера, объясненная в кибербезопасностиПодробнее
Defense Against Buffer Overflow AttacksПодробнее

What is a Buffer Overflow Attack?Подробнее

Buffer OverflowПодробнее

Practical Experience in Cybersecurity. A Dilemma (and what to do).Подробнее

Buffer Overflow ConceptПодробнее

Running a Buffer Overflow Attack - ComputerphileПодробнее
Buffer Overflow Attack Explained | How to Prevent Buffer Overflow AttackПодробнее

Buffer Overflow Hacking Tutorial (Bypass Passwords)Подробнее
Mastering Ransomware Defense: Insights from a Cybersecurity ExpertПодробнее

Exploits Explained: How Log4j, Buffer Overflows and Other Exploits WorkПодробнее
Buffer Overflow Explained. How Does Buffer Overflow Work and Why Is It Dangerous?Подробнее

Buffer Over Flow Explained and Simplified P6 - TheoryПодробнее
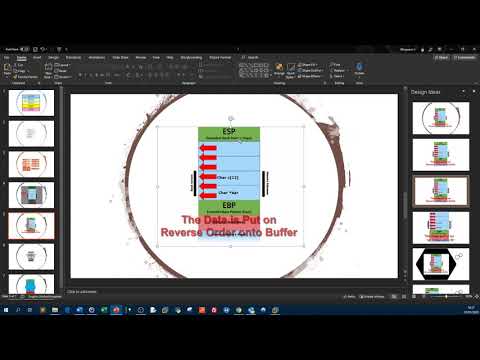
3. Buffer Overflow Exploits and DefensesПодробнее
