Defense in Depth Information Security Strategy | Layered Security | Cybersecurity Education
Defense in Depth: 5 Essential Cybersecurity Principles for Strong Architecture and 1 to Avoid GuideПодробнее

Layered security in cybersecurity. Information Systems and Controls ISC CPA ExamПодробнее

Cyber Security Full Course | Cyber Security Training | Cyber Security Tutorial| Cybersecurity GuideПодробнее
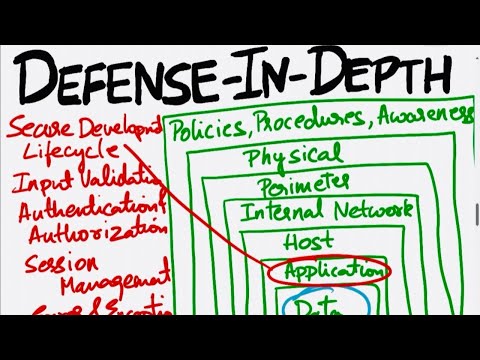
Defence in Depth | Definition & Relation to Layered Security ApproachПодробнее

What is Defense-in-Depth? | How to implement defense-in-depth| Layered Security| CybersecurityПодробнее
7 Advantages of Adopting a Defense-in-Depth Cybersecurity StrategyПодробнее

Defense in Depth | Information Security Strategy | Network Security | Cyber SecurityПодробнее

Defense in Depth in Cybersecurity. Information Systems and Controls ISC CPA examПодробнее

Defense in Depth Ultimate Cybersecurity StrategyПодробнее

Cyber Security Beginner's Course | Defense In Depth | Lecture-6 #cybercommunityПодробнее

Cybersecurity Fundamentals - Defense in DepthПодробнее

Defence in Depth: Strengthening your Cyber Security StrategyПодробнее

Multifaceted Cyber SecurityПодробнее

Webinar | Navigating the 2023 Cyber Threat Landscape: A Briefing for Business LeadersПодробнее

ISC2 CC Domain 3 : Access Control ConceptsПодробнее

Session-01 : What is Defense in Depth Core Principle ? #cybersecurityПодробнее

Cybersecurity Architecture: Five Principles to Follow (and One to Avoid)Подробнее

Defense in Depth Layers Protecting Your Information #shorts #certifiedethicalhackerПодробнее

How to Build an OT Security with Deep Defense Model by Sinclair KoelemijПодробнее

Cyber Security: Defence In Depth - Protection architecture from hackerПодробнее
