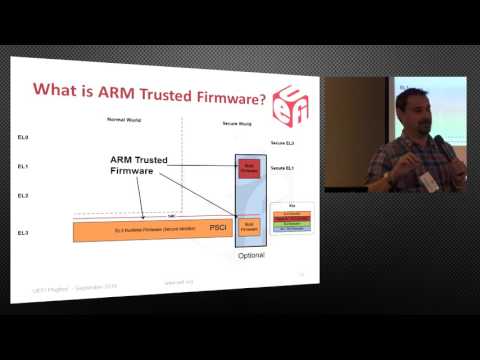
Embedded Toolbox: Create a Secure Boot Manager on Arm TrustZone in Less Than 10 Minutes

ARM Trusted Firmware ARM UEFI SCT UpdateПодробнее
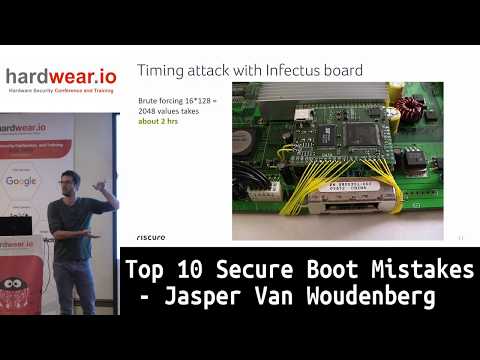
Top 10 Secure Boot Mistakes | Jasper Van Woudenberg | hardwear.io USA 2019Подробнее
DEF CON 29 - Laura Abbott, Rick Altherr -Breaking TrustZone M: Privilege Escalation on LPC55S69Подробнее
Alexandre Vicenzi: Safeguard ALP with NXP Secure BootПодробнее

Secure Boot - Embedded Security Glossary Video Series | Concurrent TechnologiesПодробнее

【M2351】TrustZone ProgrammingПодробнее

Secure Boot for IoT DevicesПодробнее

Hardwear.io NL 2023 | Breaking Secure Boot On The Silicon Labs Gecko Platform - Benoît & SamiПодробнее

Look mum, no key! Bypassing Encrypted Secure Boot | Cristofaro Mune & Niek TimmersПодробнее

Secure Boot from A to Z - Quentin Schulz & Mylène Josserand, Bootlin (formerly Free Electrons)Подробнее

Professional tools for ARM Cortex-A software developmentПодробнее

wolfBoot for STM32, Part 1: OverviewПодробнее

Secure Boot Under Attack: Simulation to Enhance Fault Attacks & Defenses by Martijn Bogaard, RiscureПодробнее

TROOPERS14 - 20 Ways Past Secure Boot - Job de HaasПодробнее

Develop Secure Cortex-M Applications with TrustzoneПодробнее

36C3 - TrustZone-M(eh): Breaking ARMv8-M's security - deutsche ÜbersetzungПодробнее

Becoming a tyrant: Implementing secure boot in embedded devicesПодробнее
