Everything you need to know about securing RDP in 30 minutes (CCB Cyber Tips)

How Fast will Hackers find your Remote Desktop #shortsПодробнее

Mastering RDP: What Is RDP, How It Works, and Secure Usage | RDP TutorialПодробнее

What is RDP and How to use it ? - Remote Desktop ConnectionПодробнее

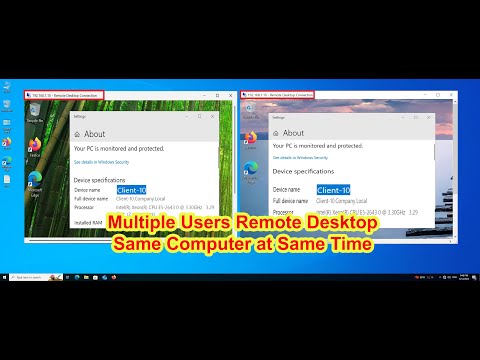
How to Allow Multiple Users to Access Remote Desktop at the Same Time on Windows 10 with RDPWrapПодробнее
Remote Desktop Protocol (RDP) Vulnerabilities and Security Best PracticesПодробнее

Remote Desktop Connection Pro TipПодробнее

Control Your PC with a Phone?Подробнее
Review and Restrict RDP Access from the InternetПодробнее

How to automatically log off idle RDP sessions or keep RDP sessions alive in Windows | VPS TutorialПодробнее

RDP Google Cloud Windows 11 – Step-by-Step Setup Guide (No Lag) 🚀Подробнее

Network security- How does RDP Work 🔐🚀Подробнее

TruGrid.com Webinar: "Forget VPN, Here's Zero Trust"Подробнее

Two Simple Ways to Stop Hackers by Securing RDPПодробнее

How to Fix Lag Issues in Remote Desktop ConnectionПодробнее
Microsoft’s RDP vulnerability - what you need to knowПодробнее
