Hack Linux, Windows System/Server (Brute Force ssh) with Metasploit | CEH v12 Tutorial
How to exploit SSH with Metsaploit? | Kali LinuxПодробнее
How Hackers Could Brute-Force SSH Credentials to Gain Access to ServersПодробнее
Metasploit For Beginners - How To Scan And Pwn A Computer | Learn From A Pro HackerПодробнее
How to Hack a Website (http 80) with Metasploit | Metasploitable v2 2023Подробнее
How A Server Can Easily Be Hacked (Metasploit)Подробнее

How To Hack and Exploit Port 22 SSH Metasploitable 2 - Home Hacking Lab Video 6Подробнее

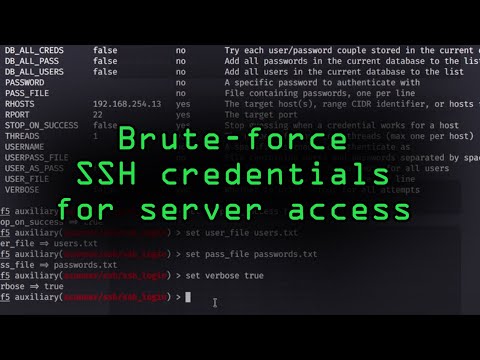
How to brute force open ssh-server logins with metasploit-framework.Подробнее

Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoCПодробнее

Free Hacking Classes | Best Hacking Guruji #hacking #cybersecurity #hacker #ethicalhackingПодробнее

How to Hack SMTP Username and Password | Metasploitable v2 2023Подробнее
Cracking SSH with Hydra on Metasploitable in Kali LinuxПодробнее

Exploiting Windows 10 | Kali Linux - Windows | LabПодробнее

Linux Privilege Escalation for Beginners | CEH v12 ILabs WalkthroughПодробнее

Ten Minute Tutorials : How to Brute Force SSH!Подробнее

Взлом SSH с помощью HydraПодробнее

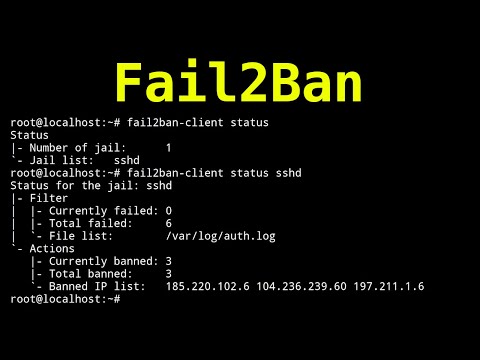
SSH Brute Force Protection With Fail2BanПодробнее
Demo Video, Unlock android device by Kali linuxПодробнее

[HID brute-force part 2] 32 passcodes tested within 12 seconds #shortsПодробнее
![[HID brute-force part 2] 32 passcodes tested within 12 seconds #shorts](https://img.youtube.com/vi/OsEWB_sQZA0/0.jpg)