Havoc C2 Framework Adopted By Hackers to Evade Windows Defender
HAVOC C2 - Demon Bypasses Windows 11 DefenderПодробнее

How Hackers Use netsh.exe For Persistence & Code Execution (Sliver C2)Подробнее
Havoc C2 & Evasive vs Microsoft Defender | FUD session Demo | AV EvasionПодробнее

Bypassing a FULLY Patched Windows 11 + Defender with a Meterpreter Shell Using ScareCrow!Подробнее

Villain C2 Framework Tutorial +(Defender Evasion).Подробнее

Havoc C2 + NimSyscallPacker = The Evasion Dream Team?Подробнее
How Hackers Bypass Windows Defender with Legitimate Files | Bypassing Windows DefenderПодробнее
Creating a .EXE Binary that FULLY Evades Windows Defender (AGAIN!) in 2024!Подробнее

Havoc C2 Framework - Setup Demonstration with Windows Defender BypassПодробнее
HAVOC C2 - Demon Bypasses Windows 11 DefenderПодробнее
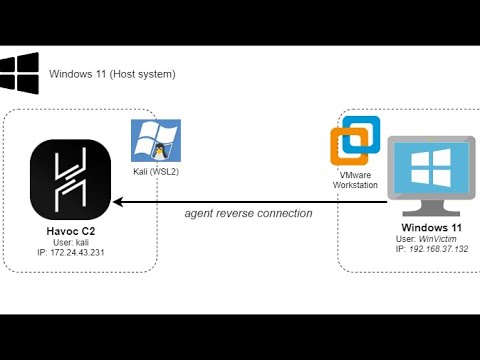
How Hackers Write Malware & Evade Antivirus (Nim)Подробнее

Windows Defender Bypass with Powershell & Invoke-ObfuscationПодробнее

Reverse Shell UNDETECTED by Microsoft Defender (hoaxshell)Подробнее

Bypassing Kaspersky EDR Optimum + Villain C2Подробнее

How to hack any widows PC with havoc C2. (+ privilege escalation)Подробнее
Red Teaming 101 - Establishing Persistence with Havoc C2 and SharPersistПодробнее

Red Teaming With Havoc C2Подробнее

Malware beats Windows Defender: How you get hackedПодробнее

How Hackers use PowerShell to EVADE Anti-Virus SoftwareПодробнее

bypassing windows defender | Malware developmentПодробнее
