How Hackers Hack sensitive data public WiFi connected Device (MITM Attack)

Cybersecurity Expert Demonstrates How Hackers Easily Gain Access To Sensitive InformationПодробнее

3 Levels of WiFi HackingПодробнее

Hacker Demonstrates Security Risks Of Free Public Wi-FiПодробнее
10 Essential Tips to Secure Your Smartphone from Hackers in 2024! #cybersecurity #onlinesafetyПодробнее

hacking every device on local networks - bettercap tutorial (Linux)Подробнее

How Hackers Can Attack You On Public Wi-Fi | NordVPNПодробнее

Pro Hacker Demonstrates hacking other devices in Free Public Wi-FisПодробнее
100 Cybersecurity Terms in (1 Hour)Подробнее

Man-In-The-Middle Attack (MITM) Live Demonstration - Wi-Fi Hacks | WiresharkПодробнее
Public Wi-Fi | Hacking the SystemПодробнее

How hackers can steal your data using simple crocodile clips? #shortsПодробнее

Hacking (redacted) PUBLIC WiFi with a Raspberry Pi and Kali LinuxПодробнее
How Hackers Spy on you from your own WiFi!Подробнее
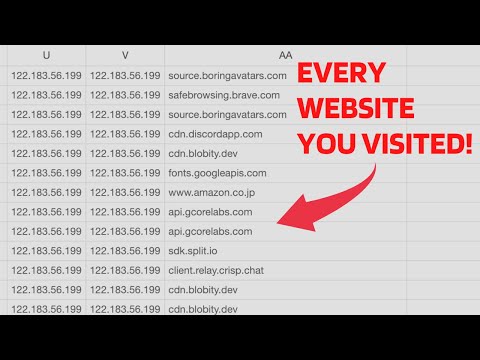
5 Ways Hackers Use Public Wi-Fi to hack youПодробнее

how Hackers SNiFF (capture) network traffic // MiTM attackПодробнее

how hackers hack your devices on wifiПодробнее

Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoCПодробнее

Ethical hacker shows us how easily smart devices can be hacked and give access to your personal infoПодробнее

This is how hackers hack you using simple social engineeringПодробнее

WiFi Hacking Watch #shortsПодробнее
