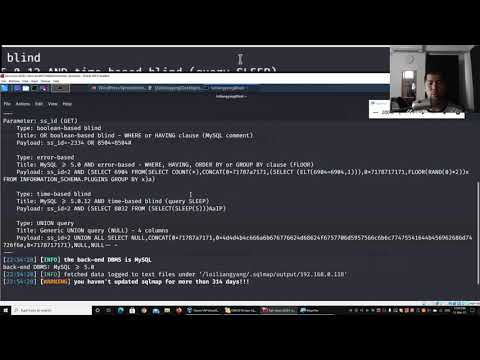
How Hackers Use Xerosploit for Advanced MiTM Attacks 2023 | HackerDigital

Man-In-The-Middle Attack (MITM) Live Demonstration - Wi-Fi Hacks | WiresharkПодробнее
Ethical Hacking: SNIFFING WITH XEROSPLOIT -- Network Security DemonstrationПодробнее

Xerosploit tutorial how inject javascript networkПодробнее

hacking every device on local networks - bettercap tutorial (Linux)Подробнее

Xerosploit Unleashed: Unraveling the Man-in-the-Middle Attack FrameworkПодробнее

mitm attacks using xerosploit (script kiddie) #escriptersПодробнее

"Unlock Cyber Power: Mastering httpx-toolkit in Kali Linux for Ultimate Pentesting!"Подробнее

How Hackers Use Xerosploit for Advanced MiTM AttacksПодробнее

How to peform mitm attack (sniff) using xerosploit with kali linux.Подробнее

Kali Linux Tutorial XerosploitПодробнее

Advanced Ethical Hacking & Cybersecurity Mastery (Part 2) | Web App Pentesting, MITM, Android HackedПодробнее

Intercept and modify network traffic EASY MITM Attack (Bettercap tutorial)Подробнее

Remove malwares from your computer in 1 clickПодробнее

how Hackers SNiFF (capture) network traffic // MiTM attackПодробнее

How Hackers take advantage of Misconfiguration | HackTheBox Jerry WalkthroughПодробнее

How Hackers Hijack Applications Using Malicious DLLs: And How To Improve Cyber Defenses Against ItПодробнее

Protect Against Hackers!Подробнее

Как защититься от MITM атак ?Подробнее

Secure your site from hackers now! let a Pro Hacker show you how!Подробнее