How to Perform a Cybersecurity Risk Assessment: Step-by-Step Guide

Risk Assessment - Step by Step GuideПодробнее

Building a Strong Cybersecurity Roadmap for Organization (Step-by-Step Guide)Подробнее

Breaking Into Every Cybersecurity Vulnerability (Step-By-Step Guide)Подробнее

How to Implement ISO 27001: A Step-by-Step Guide with ConformioПодробнее

Build Your Personal Digital Security Plan: A Step by Step GuideПодробнее

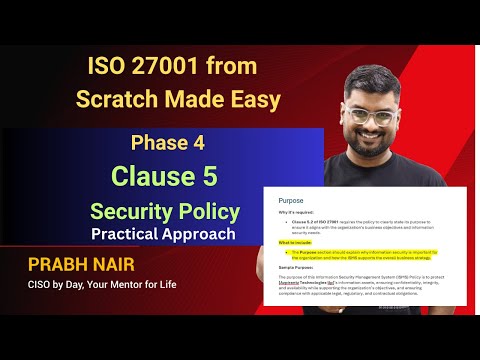
How to Write a Security Policy Compliant with ISO 27001:2022 Clause 5 | Step-by-Step GuideПодробнее
The Daisy Minute - Step by Step Guide to Festive Season Cybersecurity for BusinessesПодробнее

Master the Audit Lifecycle: Step-by-Step Guide to Effective AuditsПодробнее

How to conduct a real Risk AssessmentsПодробнее

How to Implement ISO 27001:2022 Like a Pro – Step-by-Step GuideПодробнее

Implementing Zero Trust Architecture: A Step-by-Step Guide Part 2Подробнее

Practical 62443 Based Risk Assessment Exercise - OT Security - Course OverviewПодробнее

Implementing Zero Trust Architecture: A Step-by-Step Guide Part 1Подробнее

Risk Management Made Easy: A Step-by-Step Guide to Using a Risk RegisterПодробнее

Cybersecurity For Beginners | Basics of Cyber security For Beginners Complete Course, GoogleПодробнее

ISO 27001:2022 Implementation: From Start to Finish with Case StudyПодробнее

How to Conduct Gap Assessment in ISO 27001Подробнее

Step-by-Step Cyber Risk Assessment Guide: Secure Your Digital EnvironmentПодробнее

How to Conduct an Internal Audit? A step-by-step Guide to Internal IT Audit | Internal AuditingПодробнее
