How to run reports and attack vector simulations in Microsoft Defender for IoT

Can I survive his vector attack ? Welcome to our new channel ! #1Подробнее

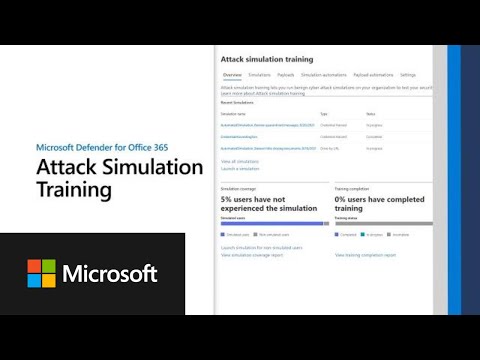
Attack Simulation Training with MicrosoftПодробнее
How to discover attack vectors using Microsoft Defender for IOTПодробнее

How to use Microsoft Defender for IOT in forensic investigationsПодробнее

All About Microsoft Defender for IoTПодробнее

Azure Defender for IoT Ep 13: Attack VectorsПодробнее

How to run reports and attack vector simulations in Azure Defender for IoTПодробнее

Demonstration of Microsoft Defender for IOT platformПодробнее

How to Assess Printers' Security Posture in Microsoft 365 Defender [Microsoft Defender for IoT Demo]Подробнее
![How to Assess Printers' Security Posture in Microsoft 365 Defender [Microsoft Defender for IoT Demo]](https://img.youtube.com/vi/cPA9Ze-jZm4/0.jpg)
Get started with simulation automations | Microsoft Defender for Office 365Подробнее

Cymulate breach and attack simulation integrates with Microsoft Defender for EndpointПодробнее

Learn How To Use The Microsoft 365 Attack SimulatorПодробнее

How to optimize and tune the Microsoft Azure Defender for IoT platformПодробнее

How to optimize and tune the Microsoft Defender for IoT platformПодробнее

Get Started Using Attack Simulation Training in Microsoft 365 DefenderПодробнее

How to analyze the Risk Assessment report in Azure Defender for IoTПодробнее
