How to use Cloud Logging to detect security breaches

Detect, Respond, and Recover from Cybersecurity Attacks | Google Cloud Cybersecurity CertificateПодробнее

Cloud Security Monitoring and Threat Detection in AWSПодробнее

Detecting S3 Breaches with PantherПодробнее

What Is Intrusion Detection System? | Intrusion Detection System (IDS) | Cyber Security |SimplilearnПодробнее

AWS This Week: CodeGuru Reviewer log injection detector, lower latency EFS, AWS Budgets auto-adjustПодробнее

Assume Breach: An Inside Look at Cloud Service Provider SecurityПодробнее

Getting Real-Time access Logs with Access Transparency (Cloud Next '18)Подробнее

Logging in the Cloud: From Zero to (Incident Response) HeroПодробнее
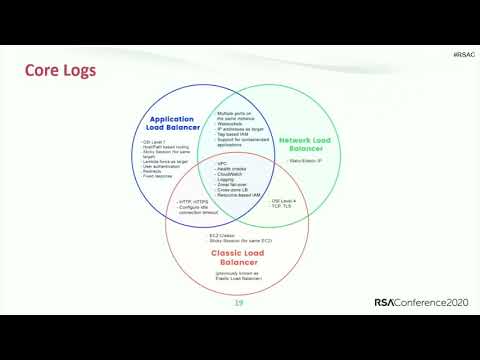
MCAS webinar: App Discovery and Log Collector Configuration | Session 4 | EUПодробнее
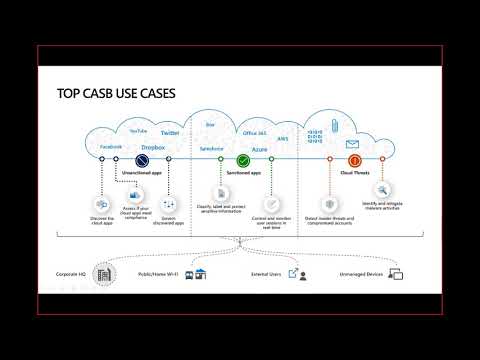
Cloud Forensics 101 (Cloud Next '18)Подробнее

Security and Compliance in Healthcare (Cloud Next '18)Подробнее
