How to use Google Dorks for finding SQL injection Vulnerability | Google dorks Sql Injection
Ultimate Exploits toolsПодробнее

SQL Injection AttackПодробнее

SQL Injection: Understanding the Risk and Protecting Your DataПодробнее
DorkSploit: Your Digital Detective Find and Scan Vulnerable WebsitesПодробнее

SQL Injection Methodology using Google Dorks | Live Bug Bounty Hunting | Live demoПодробнее

Unleashing the Power of Google Dorks: A Comprehensive Hacking GuideПодробнее

DorkПодробнее

Uncover Hidden Data with Simple Searches using Google DorkingПодробнее

SQL Injection Live Demonstration | Testing Website Vulnerabilities | SQLMapПодробнее
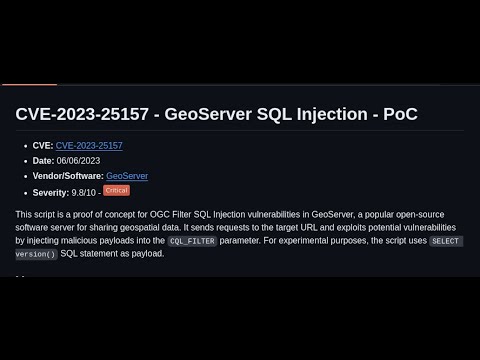
EASY $1500 CRITICAL CVE-2023-25157 - GeoServer SQL Injection - PoCПодробнее
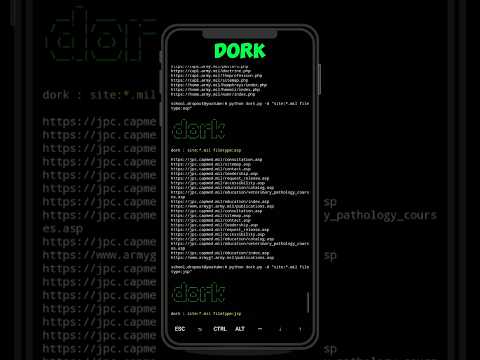
Google Dork Python Tool | Bug Bounty TipsПодробнее
SQL Injection Mystery : SQL Lab Setup| Use of Google Dork | SQL Payloads PART 02Подробнее

☃️ How to use Dork Searcher 2023 ❄️Подробнее
Implementasi Materi Nmap, Google Dork, Brute Force dan Sql InjectionПодробнее

phpMyAdmin Login Bypass || Real Website Hacking Using Google DorkПодробнее
google hacking(Dork), Nmap, DirBuster, SQL injectionПодробнее

SQL injection | SQL Dork |SQL Vulnerability | SQL Bug | SQL Vulnerability DorkПодробнее

SQL Injection Vulnerabilities on Real Websites | using SQLMap and Google DorkПодробнее

HOW TO FIND HIDDEN PARAMETERS | GOOGLE DORKS | Bug Bounty Tutorial - | Bug bounty POC | 2023Подробнее

How To Use Google Hacking Database | 2023Подробнее
