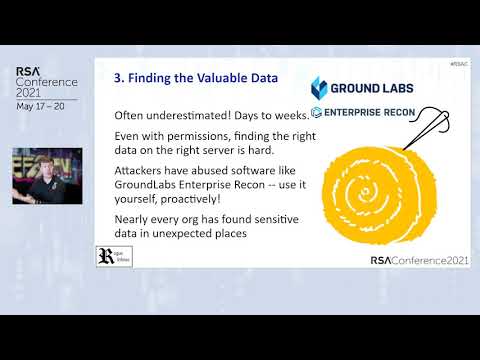
Identify and protect sensitive data, detect and respond to security incidents.
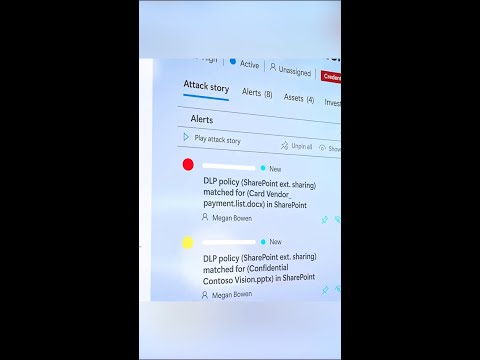
What is Security Information and Event Management (SIEM)Подробнее

EDR Interview Questions and Answers | Endpoint Detection and Response | CyberSecurity InterviewПодробнее
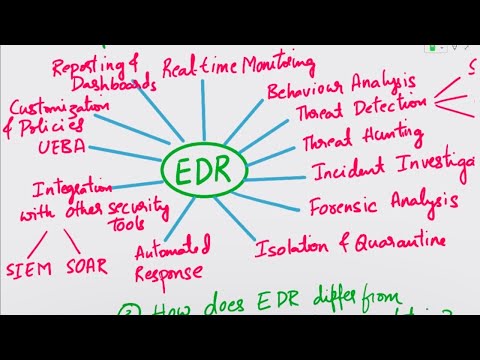
Microsoft Security for Beginners: Dark to Cloud Series 2/5 (GPT TTS) SC-900 and SC-100Подробнее

Complete Microsoft Azure Security Technologies (AZ-500) : Interview Questions and AnswersПодробнее

Basic Fundamental Cyber Network Security GuideПодробнее

Complete Cisco CBROPS (200-201) Interview Questions : Cybersecurity Operations FundamentalsПодробнее

The Benefits of Network Security Surveillance: Identify, Prevent, and ImproveПодробнее

CMMC 2.0, NIST 800-171, and Incident Response - BreachRxПодробнее

AWS re:Invent 2018: Supercharge GuardDuty w/ Partners: Threat & Response at Scale GPSTEC304Подробнее

Protect, Detect, and Respond to Solorigate using M365 Defender - Microsoft 365 Defender WebinarПодробнее

Comply with the GDPR: Detecting and responding to personal data breachesПодробнее

What's New in Cloud Data Security?Подробнее

Protecting Sensitive Data in the Cloud - David MamanПодробнее

How to pass AWS Certified Security Specialty?Подробнее

How Do You Know You Havent Already Been Breached — ILTA Webinar with NetsurionПодробнее

Top Active Directory Attacks: Understand, then Prevent and DetectПодробнее