Implementing a Custom Public Key Infrastructure (PKI)

5th International Conference on Public Key Infrastructure and its Applications (PKIA 2024) - Day 2Подробнее

Beyond secrets, using Vault to automate PKIПодробнее

Public Key Infrastructure - CompTIA Security+ Sy0-701 - 1.4Подробнее

How to use Public Key Infrastructure (PKI) with HashiCorp Vault | HashiCorp Vault 101Подробнее

Deploying A Multi-Tier PKI (Public Key Infrastructure) Inside an Active Directory Domain Using ADCSПодробнее

How to Implement Public Key Infrastructure (PKI) Solutions and CryptographyПодробнее

CompTIA Security+ Full Course: Public Key Infrastructure (PKI)Подробнее

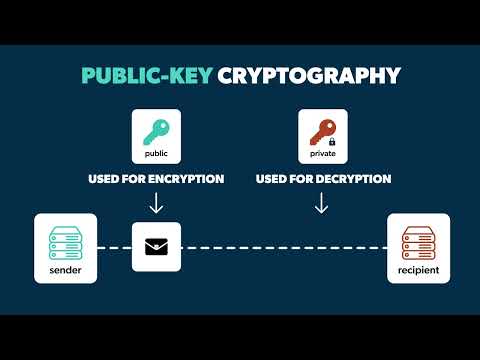
What Is Public Key Infrastructure (PKI)?Подробнее
CompTIA Security+ Practice Exam Part 4Подробнее

[Module 25 - Implementing a Public Key Infrastructure]Подробнее
![[Module 25 - Implementing a Public Key Infrastructure]](https://img.youtube.com/vi/n2xXbzv0HHI/0.jpg)
AWS re:Invent 2020: Do you need an AWS KMS custom key store?Подробнее

Getting Started with PSPKI - Certificate Authority Automation!Подробнее

AWS re:Inforce 2019: Achieving Security Goals with AWS CloudHSM (SDD333)Подробнее

Implementing a Public Key InfrastructureПодробнее

Meraki SAML IntegrationПодробнее

Getting Started with Spring Authorization ServerПодробнее

CIS 352 - Chapter 7 - PKI and Cryptographic ApplicationsПодробнее

Azure Network Security webinar: Content Inspection Using TLS Termination with Azure Firewall PremiumПодробнее

Module 8 - Implementing Cryptography - Configure a Public Key InfrastructureПодробнее
