Insecure SSO implementation - vulnerability discovery and exploit

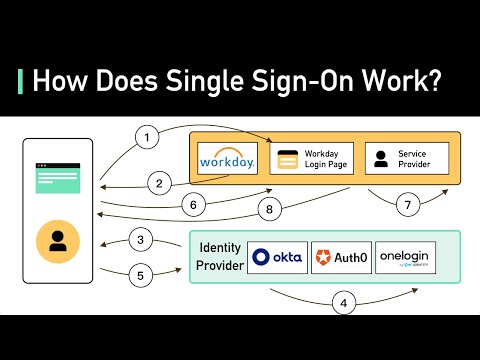
What Is Single Sign-on (SSO)? How It WorksПодробнее
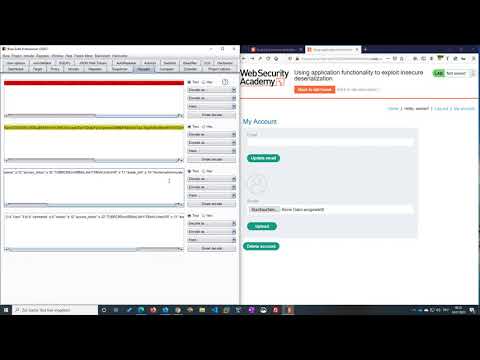
Using application functionality to exploit insecure deserialization (Video solution)Подробнее
Insecure Design Vulnerability Explained with Instagram Hack Example | Owasp Top 10Подробнее

2021 OWASP Top Ten: Insecure DesignПодробнее

Was Vulnerability Management Stressful?Подробнее

How Can I Fix XSS Vulnerabilities in JSP with ESAPI Validator?Подробнее

Identity Theft: Attacks on SSO SystemsПодробнее

Insecure Deserialization ExploitПодробнее

Explaining Insecure Deserialization Vulnerability - COMPTIA Pentest+ TryHackMe OWASPПодробнее

BYPASSING SAML AUTHENTICATION FOR BEGINNERS!Подробнее

Hacking SSO: OverviewПодробнее

CORS vulnerability with trusted insecure protocols (Video solution)Подробнее

Insecure Design In OWASP #shorts #insecure #vulnerabilitiesПодробнее

OSCP Exploitation Guide to Insecure DeserializationПодробнее

Exploit Insecure Direct Object References (IDOR)Подробнее

Method To Prevent Insecure Deserialization - OWASP VulnerabilityПодробнее

Exploit Java Deserialization | Discovering Insecure DeserializationПодробнее
Insecure Deserialization Vulnerability in Hindi | Spin The Hack Pathshala Video Demo🔥Подробнее

Ivacy VPN Insecure Design Vulnerability PoCПодробнее
