intro to cloud hacking | getting usernames and passwords
hacking the cloud | getting usernames and passwordsПодробнее

DEF CON 25 - Gerald Steere, Sean Metcalf - Hacking the CloudПодробнее

Protect Your Websites Now! Watch How Hackers Access Database for Usernames and PasswordsПодробнее

This is How Hackers Crack Passwords!Подробнее
How to Get Someone's PasswordПодробнее

intro to cloud hacking (leaky buckets)Подробнее

5 Quick Tips to Secure Your Online Accounts | Cybersecurity Guide | #onlinesafety #cybersecurityПодробнее

Hacking Usernames and Passwords | Web Security AcademyПодробнее

Hacking with Google Cloud ShellПодробнее

How Hackers Login To Any Websites Without Password?!Подробнее

Cloud Hacking: The BasicsПодробнее

How Hackers Hack Websites Usernames and Passwords?! remote code executionПодробнее

Get started with Azure pentestingПодробнее

how hackers hack any website in 9 minutes 6 seconds?!Подробнее

Cloud Hacking: Hacking Amazon AWSПодробнее

Cloud Security Explained! Hear from a Pro Hacker!Подробнее
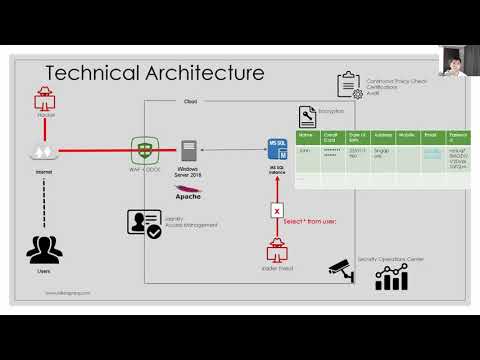
How to get started in Cloud HackingПодробнее

5 Powerful Cloud Hacking Tools You Need to Know #shorts #cybersecurityПодробнее

Part 1: Malicious File vs Username and Passwords | Keylogger #cybersecurity #hacking #ai #hackerПодробнее

Example of an AWS HackПодробнее

How Easy Is It For Hackers To Brute Force Login Pages?!Подробнее
