Intro to JWT Vulnerabilities
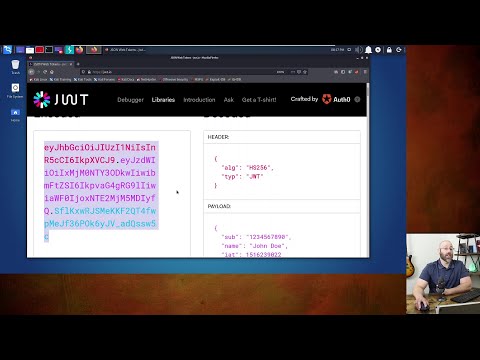
Mastering JWT Security: Identify and Mitigate VulnerabilitiesПодробнее

Cracking a JWT with MD5_HMAC Algorithm - Marmalade 5 [NahamCon CTF 2023]Подробнее
![Cracking a JWT with MD5_HMAC Algorithm - Marmalade 5 [NahamCon CTF 2023]](https://img.youtube.com/vi/3LRZsnSyDrQ/0.jpg)
JWT Authentication Bypass via kid Header Path TraversalПодробнее

JWT Authentication Bypass via Algorithm ConfusionПодробнее
Understanding JWT Vulnerabilities: The 'None' VulnerabilityПодробнее

JWT Authentication Bypass via jku Header InjectionПодробнее
JWT Authentication Bypass via jwk Header InjectionПодробнее
How to Exploit "Json Web Token"(JWT) vulnerabilities | Full PracticalПодробнее

[HINDI] Introduction to JWT | JSON Web Token | Security Concerns of JWTПодробнее
![[HINDI] Introduction to JWT | JSON Web Token | Security Concerns of JWT](https://img.youtube.com/vi/5mUDRQfwXuE/0.jpg)
Understanding and Safeguarding JWT: Exploring VulnerabilitiesПодробнее

Introduction to JWT AttacksПодробнее

what is jwt token authentication | attacking jwt for beginnersПодробнее
