Microsoft Endpoint Manager Intune Endpoint Protection Part II Antivirus
Microsoft Defender for Endpoint Tutorial | Microsoft Defender for Endpoint Interview Questions | MDEПодробнее

Configure Microsoft Defender for Endpoint Antivirus on MacOSПодробнее

Defender for Business VS Microsoft Defender for EndpointПодробнее

Microsoft 365 Defender for Endpoint? Good Enough for your Business?Подробнее
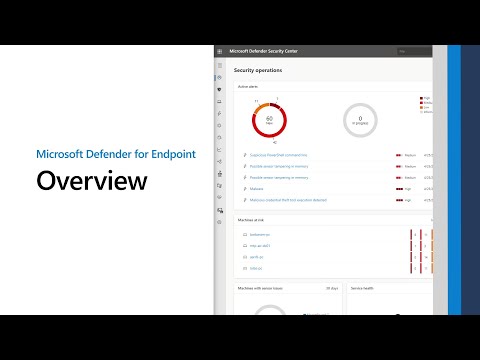
Microsoft Defender for Endpoint OverviewПодробнее

Microsoft Endpoint Manager Intune Configuration Profiles Part II WindowsПодробнее

Building a tamper-resilient endpoint with Microsoft Intune and Microsoft DefenderПодробнее

50. How to Configure Microsoft Defender Antivirus Policy with IntuneПодробнее

How to Configure and Deploy Microsoft Defender for Endpoint using IntuneПодробнее

45. How to Apply Security Baseline Policy in Microsoft IntuneПодробнее

Security Management with Defender for EndpointПодробнее

Endpoint Protection Part 6 - Windows Defender Exploit Guard PoliciesПодробнее

Microsoft Endpoint Manager: Endpoint SecurityПодробнее

Endpoint Protection Part 5 - Defender Advanced Threat Protection (ATP) PoliciesПодробнее

MEMUG January 2022 - Endpoint Protection with MicrosoftПодробнее

Microsoft Defender for Endpoint OverviewПодробнее
Configure Microsoft Defender Application Control using Intune Endpoint Security profilesПодробнее

Manage unenrolled Windows devices with Microsoft Defender for EndpointПодробнее

Endpoint Protection Part 8 - Windows Defender Application Control (WDAC) PoliciesПодробнее

Endpoint Protection - Part 7 Windows Defender Application Guard PoliciesПодробнее
