One Line of Code can open you for a MITM attack, Let us Discuss

What is a Man-in-the-Middle Attack? (In About A Minute)Подробнее
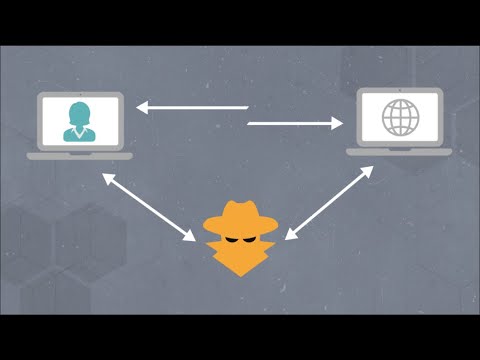
Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoCПодробнее

This is how hackers hack you using simple social engineeringПодробнее

USMC Drill Instructors Unleashed 😳💀🇺🇸Подробнее

How Hackers are Hacking Your Phone via BluetoothПодробнее

🚀Master.NET 8 Microservice: Manage Security🔐with JWT, Restrict API Calls to Gateway, Caching & More🌟Подробнее

Flipper Zero: Beginner GuideПодробнее

Bro tells the Drill Sergeant what to doПодробнее

linux users be likeПодробнее
MiTM Attack | ARP Spoofing | ARP Poisoning in Kali LinuxПодробнее

iPhone and Android WiFi Man-in-the-middle attack // PYTHON Scapy scripts for attacking networksПодробнее

Unlock Any Device By Termux #short #youtubeshorts #trending #viralПодробнее
how Hackers SNiFF (capture) network traffic // MiTM attackПодробнее

I HACKED my Internet Service Provider's router. So I could get rid of it.Подробнее

Powerful WiFi hacking tool (wifite) [Tutorial]Подробнее
![Powerful WiFi hacking tool (wifite) [Tutorial]](https://img.youtube.com/vi/LK6w2xXm71k/0.jpg)
Man-in-the-middle attack EXPLAINED: HOW can you to prevent MITM attackПодробнее

Cybersecurity Expert Demonstrates How Hackers Easily Gain Access To Sensitive InformationПодробнее

3 Levels of WiFi HackingПодробнее
