OWASP TOP 10 needed for Cloud Security?
OWASP Top 10 | Build With AI #technology #kalilinux #cybersecurity #kalilinuxtools #crypto #kalinuxПодробнее

Common SSRF misconceptions during the interviews - OWASP top 10Подробнее

AWS re:Invent 2024 - Mitigating the OWASP Top 10 for LLMs: Build secure gen AI applications (AIM283)Подробнее

System Design 31 Application Security Web Mobile Desktop Cloud OWASP NIST Cybersecurity XSS CSRFПодробнее

AWS re:Inforce 2024 - Mitigate OWASP Top 10 for LLM risks with a Zero Trust approach (GAI323)Подробнее

OWASP Top 10 | A08:2021-Software and Data Integrity Failures | Cyber security 2024Подробнее

Kirk Jackson - OWASP Top 10 OverviewПодробнее

OWASP Top 10 Proactive Controls 2024 - C5: Secure By Default ConfigurationsПодробнее

How Effective is AWS WAF in Mitigating OWASP Top 10 VulnerabilitiesПодробнее

OWASP Top 10 #1 Broken Access ControlПодробнее

OWASP Top 10 | A02- Cryptography failure Introduction | Cyber security 2024Подробнее

GDG Cloud Southlake 29 Jimmy Mesta OWASP Top 10 for KubernetesПодробнее
Mastering Cybersecurity: Essential OWASP Guidelines for Effective ProtectionПодробнее

Defending Your Cloud Native Apps Against the Serverless Top 10 By Chris KoehneckeПодробнее

OWASP Top 10 | A05 - Security Misconfiguration | Cyber security 2024Подробнее

Flagship Projects OWASP Cloud Native Application Security Top 10 Flagship Project Ron ViderПодробнее

OWASP Mobile Top 10 Risks (2024) | Detailed Explaination with Examples | PayatuПодробнее

OWASP Top 10 | A04 - Insecure Design | Cyber security 2024Подробнее

OWASP Algiers @ SecuriCON | Securing Multi-Cloud Environments: Best Practices & ChallengesПодробнее

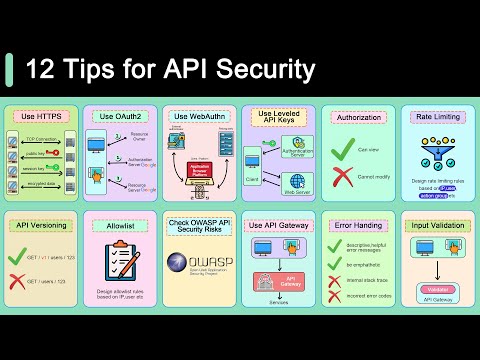
Top 12 Tips For API SecurityПодробнее