Permission to Hack You: Illicit Consent Grant Attack

Attack Demonstration - Illicit consent grant attack in Azure AD / Office 365Подробнее

365-Stealer Introduction/Guide VideoПодробнее

This Hacker Saved the InternetПодробнее

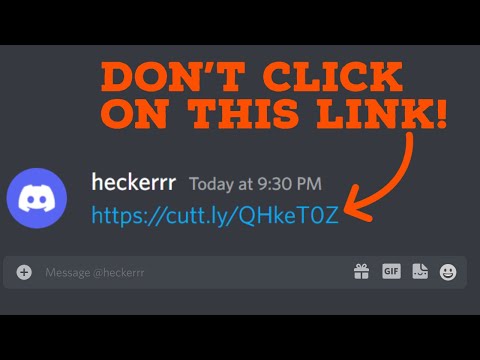
This is how Hackers can *OWN YOU* with just a link!Подробнее
Ethical hacker shows us how easily smart devices can be hacked and give access to your personal infoПодробнее

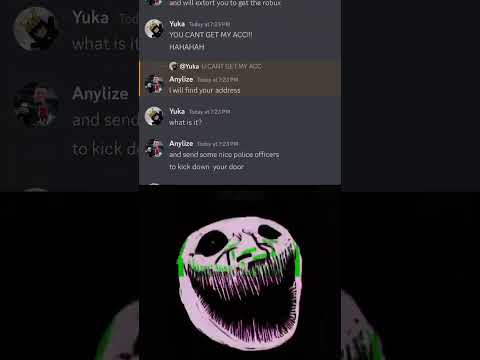
EXPOSING A ROBLOX HACKER ON DISCORDПодробнее
Demonstration - Illicit consent grant attack in Azure AD / Office 365Подробнее

DEF CON 29 - Jenko Hwong - New Phishing Attacks Exploiting OAuth Authentication FlowsПодробнее

This is how hackers hack you using simple social engineeringПодробнее

i got hacked on discord - here's what NOT to do.Подробнее

Make Yourself Look Like A Professional HackerПодробнее
Watch This Russian Hacker Break Into Our Computer In Minutes | CNBCПодробнее

How to hack WebCamsПодробнее

How to be a hacker in 1 minute 😎 #shortsПодробнее
Do you know this Gmail hack??Подробнее

I hacked time to recover $3 million from a Bitcoin software walletПодробнее

How to make it look like you’re hacking! #shortsПодробнее

Hacking Linux with These Simple Commands Pt:1Подробнее
Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoCПодробнее
