PH2 D2S3 - Attack Vectors
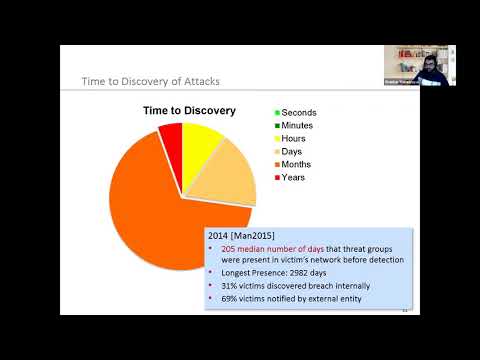
Attack Vector, Wireless, Email, Supply ChainПодробнее
Cyber Threats & Attack Vectors Explained – Stay Safe Online!Подробнее

Decoding Cyber Attack Vectors: Revealing Secrets Hackers Keep HiddenПодробнее

Common Kubernetes Attack Vectors and How to Secure Your C... Catherine Heatherly & Danielle ChappellПодробнее

Daily Bullets Episode 3 - Understanding Attack Vectors in the Cyber DomainПодробнее
This Attack Vector is EvilПодробнее

Cyber Threats and Attack Vectors (CYB-505)Подробнее
2.1 Cyber Threats and Attack VectorsПодробнее

sigint10 attack vectors against mobile devicesПодробнее

ATTACK VECTORПодробнее

Attack Vectors & Attack SurfaceПодробнее

5 Code Smells & Attack VectorsПодробнее

Foundations of Cybersecurity 2-2: Common Attack VectorsПодробнее
Cybersecurity Fundamentals DNS Attack VectorsПодробнее
The Anatomy of an Attack - Understanding Attack VectorsПодробнее

Attack Vectors | Fundamentals of Cybersecurity ( Tutorial 02)Подробнее
Phishing, the Most Common Attack Vector | Cyber Insurance AcademyПодробнее

004 Information Security Threats And Attack VectorsПодробнее
