Protect Your Privacy: The Dangers of IoT Devices
Securing loT Devices: Protecting Your Smart Home|Best Practices for Securing IoT Devices"Подробнее

How Hackers Exploit IoT Devices and How to Defend Against AttacksПодробнее

Data And Privacy | Risks in IoT (Internet of Things) Devices | Tips for Better Information SecurityПодробнее

Protection Of IoT #iotsecurity #cybersecurity #privacy #safety #technology #innovationПодробнее

Is your smart home security system putting you at risk? | Don’t try this at home, episode 2Подробнее

DEF CON 31 - Vacuum Robot Security & Privacy Prevent yr Robot from Sucking Your Data - Dennis GieseПодробнее

Securing Your IoT DevicesПодробнее

IoT Devices: Managing Data Privacy RisksПодробнее

IoT Security Risks & PrivacyПодробнее

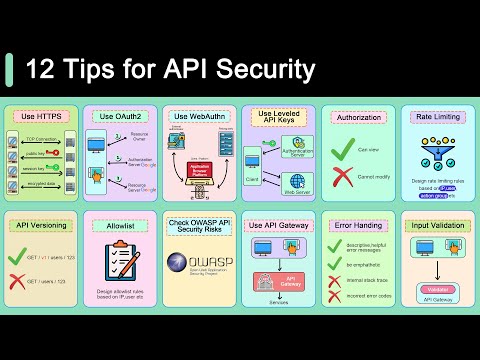
Top 12 Tips For API SecurityПодробнее
IoT Nightmares: Protect Your Smart Home Before Hackers Take ControlПодробнее

UX design and Data Protection series: How can we design online products for safety?Подробнее

Your Smart Home Is Stupid - IoT Security ExplainedПодробнее

Protecting Your Hospital From IoT and Connected Medical Device Security ThreatsПодробнее

USENIX Enigma 2022 - Leveraging Human Factors to Stop Dangerous IoTПодробнее

Tracking your health data through wearable devicesПодробнее

You NEED to learn about FIREWALLS!Подробнее

Internet of Things (IoT): Definition, Advantages, Disadvantages, and Security ConsiderationПодробнее

Do IoT Devices Make Your Network Unsecure? | Security, Attacks & Best Practices | CybersecurityПодробнее
