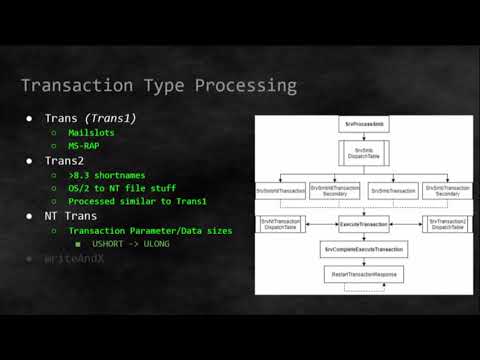
Reading Kernel Source Code - Analysis of an Exploit

this SSH exploit is absolutely wildПодробнее

37C3 - Operation Triangulation: What You Get When Attack iPhones of ResearchersПодробнее
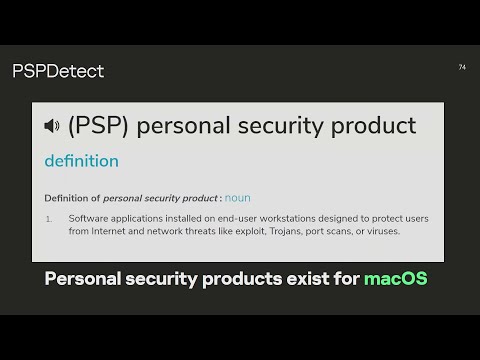
37C3 - Writing secure softwareПодробнее
#HITB2021SIN D1T1 - Exploiting UAF By Ret2bpf In Android Kernel - Xingyu Jin & Richard NealПодробнее

new vulnerability in your motherboard lasts foreverПодробнее

OpenSSH backdoor'ed via XZ & Systemd on RedHat & Debian systemd: multi-year effort by state actor?Подробнее
DEFCON 19: Kernel Exploitation Via Uninitialized StackПодробнее

SerenityOS exploit analysis: braindeadПодробнее

OS hacking: Let's exploit ELF symbolication to read kernel memory!Подробнее

DEF CON 26 - Bai and Zheng - Analyzing and Attacking Apple Kernel DriversПодробнее

DEF CON 26 - zerosum0x0 - Demystifying MS17 010 Reverse Engineering the ETERNAL ExploitsПодробнее