Setting Up A Cyber Lab | Metasploitable | Easy Method | Ethical Hacking | Vulnerable Machine

Simple Penetration Testing Tutorial for Beginners!Подробнее

Simple Penetration Metasploitable 2 (Cybersecurity)Подробнее
Setting Up Metasploit vulnerable machine - Ethical Hacking courseПодробнее

Ethical Hacking Lab: Downloading and Installing Metasploitable 3 - Vulnerable Ubuntu MachineПодробнее

Watch This Russian Hacker Break Into Our Computer In Minutes | CNBCПодробнее

how to build a HACKING lab (to become a hacker)Подробнее
Metasploit For Beginners - How To Scan And Pwn A Computer | Learn From A Pro HackerПодробнее
Configuring Metasploitable & Lab Network Settings | Hacking Penetration Testing From ScratchПодробнее

Gaining Access - Web Server Hacking - Metasploitable - #1Подробнее
how to get remote access to your hacking targets // reverse shells with netcat (Windows and Linux!!)Подробнее

Easy Metasploitable SetupПодробнее

Ethical Hacking Lab: Step-by-Step Metasploitable 3 Win2k8 Installation with Added VulnerabilitiesПодробнее

Metasploit Tutorial for BeginnersПодробнее
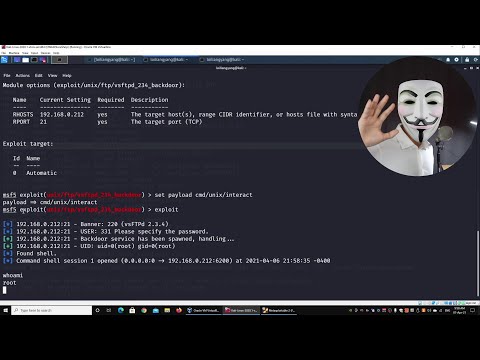
Setting up a Ethical Hacking Lab using Kali 2021.1 & metasploitable3Подробнее

Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoCПодробнее
