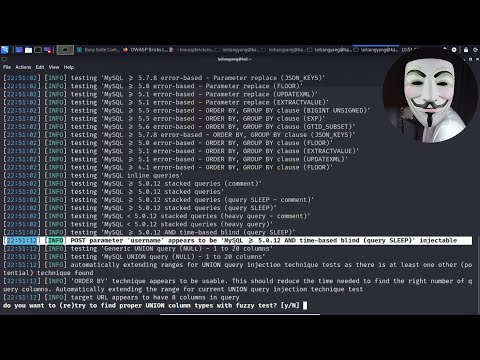
SQL Injections using Manual and Automated tools

Manual Exploitation of Common SQL Injections (Playground and CheatSheet Included)Подробнее

$5000 Bounty Time-Based SQL Injection Manual Exploitation | Bug Bounty POC | delays & Info retrievalПодробнее
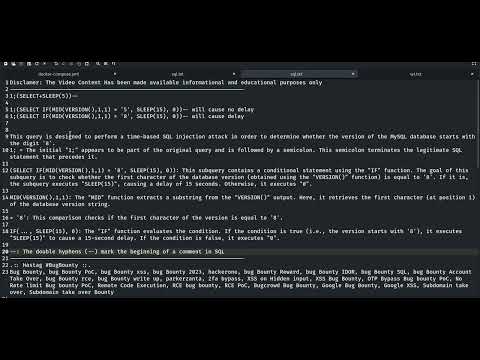
HBSQLI Automated Tool For Testing Header Based Blind SQL InjectionПодробнее

5.1 SQL Injection DVWA Low Difficulty Walkthrough | Web Security for BeginnersПодробнее

Learn Fully Automated SQL Injections In ONLY 15 Minutes!Подробнее

SQL Injection Attacks Using OWASP Zap FuzzerПодробнее

Website Hacking with SQL Injection using KALI LINUX / TERMUX - Complete TutorialПодробнее

[Hindi] SQL Injection Attack Explained | Practical Demo | SQLiПодробнее
![[Hindi] SQL Injection Attack Explained | Practical Demo | SQLi](https://img.youtube.com/vi/lwqACxcFOO0/0.jpg)
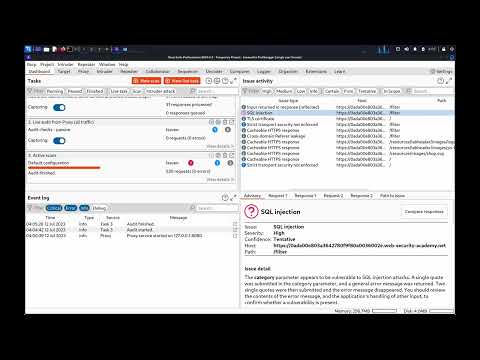
Testing for SQL injection vulnerabilities with Burp SuiteПодробнее
Top Security Testing Tools 2021 | Security Testing | Software Testing | Master YourselfПодробнее
Beginner's Guide to sqlmap - Full CourseПодробнее

Website Database Hacking using sqlmap tool | Ethical Hacking - SQL Injection AttackПодробнее
SQL Injection | Manual exploitation | Automated exploitation | Mitigation | OWASP Top 10Подробнее

BUG BOUNTY HUNTING: IDENTIFY SQL INJECTION ON LIVE WEBSITEПодробнее

SQL Injection | Complete GuideПодробнее

Ethical Hacking Tutorial: Basic concept of SQL injection Part 1Подробнее

Web Hacking Live Class 07:SQL Injection Full Bangla Tutorial Part 01 | SQL Injection for Bug-BountyПодробнее

Sqlmap Tutorial in Depth | How to Use Sqlmap | SQL Injection With SqlmapПодробнее

SQL Injection For BeginnersПодробнее