Storing IoT data securely: Various approaches and challenges

Has My IoT Device Been Hacked? Establishing Trust w/ Remote Attestation • Edlira Dushku • GOTO 2023Подробнее

Securing Your IoT DevicesПодробнее

IoT | Internet of Things | What is IoT ? | How IoT Works? | IoT Explained in 6 Minutes | SimplilearnПодробнее
Securing IoT: Challenges and SolutionsПодробнее

What Are The Biggest IoT Security Risks And Challenges? - SecurityFirstCorp.comПодробнее

Approaches to Privacy and Security for IoT Devices in a GDPR WorldПодробнее

Designing secure IoT productsПодробнее

Security for IoT on Android Things (Google I/O '17)Подробнее

How to Discover and Secure IoT Devices in the Enterprise Environment | Microsoft Defender for IoTПодробнее

5 Steps to Securing Your IoT Device in the Internet of ThingsПодробнее

Solving IoT Data Management ChallengesПодробнее

What is IoT | IoT Security Issues and Challenges | Security MethodsПодробнее

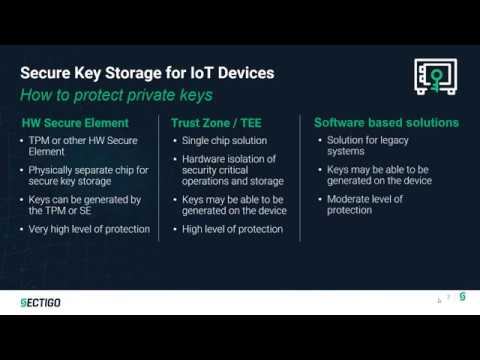
Secure Key Storage for IoT DevicesПодробнее
Securing IoT Systems with a Root of Trust | SynopsysПодробнее

Coding for 1 Month Versus 1 Year #shorts #codingПодробнее
Fundamental Challenges to IOT Data ManagementПодробнее

IoT Data Types and ChallengesПодробнее

Techugo - Ways to Secure Data on IOT DevicesПодробнее

Unlocking Ethical Hacking: Module 20 Part 01 ExplainedПодробнее

Securing the IoT Universe: Navigating the Challenges of Connected DevicesПодробнее

Creating an IoT Data Layer for Collecting, Storing, Analyzing - David SimmonsПодробнее

Securing your IoT Devices - Challenges and Way ForwardПодробнее

Security Challenges in the IoT Landscape - Podcast with IoT For AllПодробнее
