The Top 5 Most Secure Encryption Methods | 2024 Guide#Cybersecurity #Encryption #DataProtection

7 Cryptography Concepts EVERY Developer Should KnowПодробнее

Do you know the difference between the encryption algorithms? #shorts #encryption #tls #vpnПодробнее

if you use Signal, do this NOWПодробнее

Why Data Encryption is Essential for Cybersecurity Professionals in 2024!Подробнее

The Top 10 Most Secure Encryption MethodsПодробнее

Digital Privacy: Securing the Future 🔒 #DigitalPrivacy #DataProtection #shortsПодробнее

India ka top cyber security. #interview #motivation #drishti #upsc #viral #video #shortsПодробнее

What is encryption?Подробнее

You need to use Data EncryptionПодробнее

Network Fort Data Protection Feature #cybersecurity #dataprotection #featuresПодробнее

Data Encryption | Cybersecurity | CBROPS #cybersecurity #hacker #reelsПодробнее

What Is Encryption? A Beginner's Guide to Data ProtectionПодробнее

How Encryption Works - and How It Can Be BypassedПодробнее

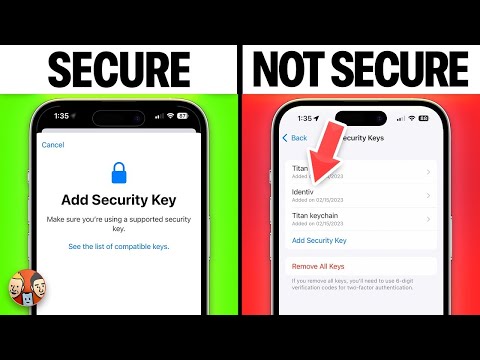
Your iPhone Isn't Secure - Do This Now!Подробнее
"🔓💻 How to Use Steganography for Cybersecurity & Ethical Hacking in 2024 Hidden Data Protection! 🔍🛡️Подробнее

Cyber Security | Asymmetric Encryption #asymmetricencryption #shorts #viralshorts #vulnerabilityПодробнее

The Encryption Secrets of Ransomware Attackers! #shorts #ytshorts #youtubeshorts #ransomwareПодробнее

Data Encryption: Keeping Information Safe #cybersecurity #data #encryptionПодробнее

Top Cybersecurity Tips for a Strong Human Firewall #firewall #cybersecurity #technology #protectionПодробнее

Cyber Security Encryption - Poll PostПодробнее
