Understanding token stealing and impersonation (Part 18)

Pivoting, port forwarding, token stealing and impersonation (overview) (Part 22)Подробнее

Use steal token and Incognito to impersonate accounts (Part 21)Подробнее
DARKEXEC - User Impersonation, Token Stealing and Grabbing User SessionПодробнее

Tiny Trump steals the showПодробнее

Windows Privilege Escalation - Token Impersonation With RoguePotato & PrintSpooferПодробнее

unmissable gag by jethroПодробнее

Protecting Your API from App Impersonation: Token Hijacking Guide and Mitigation of JWT TheftПодробнее

Pivoting, port forwarding, token stealing and impersonation (introduction) (Part 16)Подробнее

Stealing an Access Token using WinDbgПодробнее

What is the difference between Access Token , SID , Impersonation Token?Подробнее

Ethical Hacking: Token Impersonation (CSTA v5 Training Course Video Excerpt)Подробнее

Beavis and Butt-Head in parenthoodПодробнее

What is Domain Impersonation? | Tessian ExplainsПодробнее

Email Impersonation SecurityПодробнее

18. Socially Malicious: Discord as Malware Infrastructure by David ElПодробнее

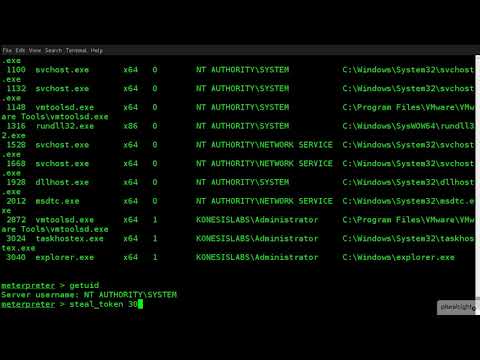
Meterpreter - Using incognito to steal access tokenПодробнее

Windows Pentesting Lab Walkthrough: Privilege Escalation: ImpersonateПодробнее

Rafael Nadal stopped by security | Wide World of SportsПодробнее
