Unmasking Cyber Threats: Understanding Man in the Middle Attacks (MiTM)

What is a Man-in-the-Middle Attack? (In About A Minute)Подробнее
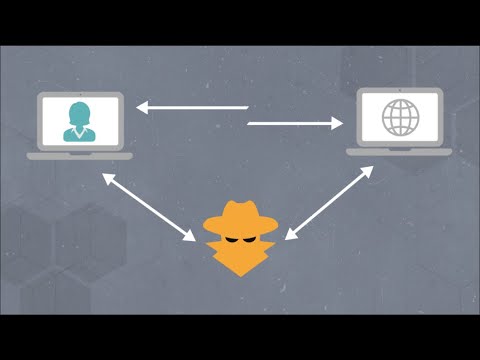
MITM Attack Explained In Hindi - Tutorial For BeginnersПодробнее

Caught in the Middle Understanding Man in the Middle AttacksПодробнее

Man-in-the-middle (MITM) Attack - 1 min AnimationПодробнее

What is a Man-in-the-Middle Attack?Подробнее

What is a Man-in-the-Middle (MITM) Cyber Attack? : Simply Explained!Подробнее

Understanding Man-in-the-Middle AttacksПодробнее

Man in the Middle (MitM) Attacks Unmasking the Invisible ThreatПодробнее

Unmasking the Invisible: Man in the MiddleПодробнее

RCS allows MITM attack -- messages can be intercepted and modifiedПодробнее

Understanding MitM attacksПодробнее

Man-in-the-middle Attacks Explained | NordVPNПодробнее
What Is A Man-in-the-Middle Attack?Подробнее

Man-In-The-Middle AttacksПодробнее

Exploring the Intricacies of Man-in-the-Middle Attack 😱 | MITM Demystified #codebombПодробнее

Man in the Middle Attack | Cybersecurity | VAPTПодробнее

Man-in-the-middle attack EXPLAINED: HOW can you to prevent MITM attackПодробнее

Man in the middle (MITM) Attack Explained & SimulatedПодробнее

25 Detect MitM Attacks Part 01Подробнее
