Unveiling Man-in-the-Middle Attacks | CEH Chronicles Ep. 4#cybersecurity

Day in the life of a cybersecurity consultantПодробнее

Cyber security Man in the middle attack #cyber #animation #cybersecurityПодробнее

CIA Spy EXPLAINS Mossad’s Ruthless Tactics 🫣 | #shortsПодробнее

CyberSecurity Definitions | Man in the Middle AttackПодробнее

🔒 Join Cyber Security Hands-on Training with Certification | CEH v12 🔒Подробнее

What is Man in the middle attack? #cybersecurity #shorts #middleПодробнее

Cybersecurity Expert Demonstrates How Hackers Easily Gain Access To Sensitive InformationПодробнее

Ethical Hacking Guide for Beginners | Learn Ethical Hacking #ytshortsindia #ethicalhacking #shortsПодробнее
What is MITM AttackПодробнее

What is man in the middle attack in cybersecurity? How it works? #cybersecurity #shortsПодробнее

Cyber Security Shark Tank: MITM AttackПодробнее

Cybersecurity Tutorial | Demo On Man In The Middle Attack | Cybersecurity Training | EdurekaПодробнее

What is a Man-in-the-Middle Attack? (In About A Minute)Подробнее
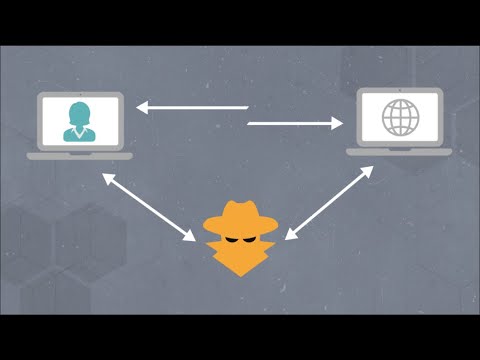
How Man-In-The-Middle Attacks Works #shortsПодробнее

#1 Ethical Hacker in The World Explains The Dark WebПодробнее
