USENIX Security '15 - Automatic Generation of Data-Oriented Exploits
USENIX Security '22 - FUGIO: Automatic Exploit Generation for PHP Object Injection VulnerabilitiesПодробнее

USENIX Security '15 - Cache Template Attacks: Automating Attacks on Inclusive Last-Level CachesПодробнее

Kotlin Encapsulation Simplified: Master Data Protection (Ep 13) | Beginner's Step-by-Step GuideПодробнее

USENIX Security '18 - Automatic Heap Layout Manipulation for ExploitationПодробнее

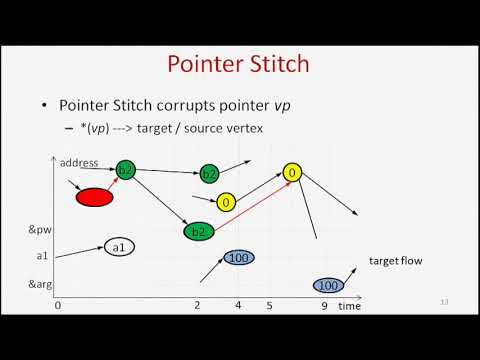
USENIX Security '15 - Automatic Generation of Data-Oriented ExploitsПодробнее
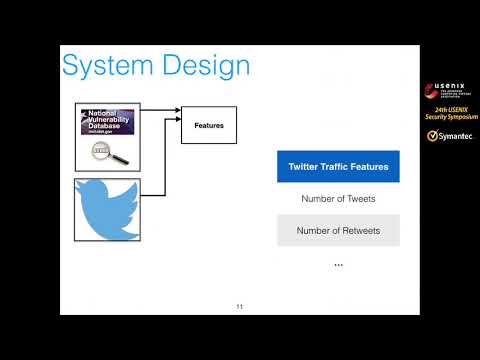
USENIX Security '15 - Vulnerability Disclosure in the Age of Social Media: Exploiting Twitter...Подробнее
USENIX Security '24 - Practical Data-Only Attack GenerationПодробнее

USENIX Security '24 - UBA-Inf: Unlearning Activated Backdoor Attack with Influence-Driven CamouflageПодробнее

USENIX Security '20 - Automatic Techniques to Systematically Discover New Heap ExploitationПодробнее

USENIX Security '15 - Trends and Lessons from Three Years Fighting Malicious ExtensionsПодробнее

Automatic Exploit Generation OverviewПодробнее

USENIX Security '15 - Compiler-instrumented, Dynamic Secret-Redaction of Legacy Processes...Подробнее

USENIX Security '15 - EASEAndroid: Automatic Policy Analysis and Refinement for Security Enhanced...Подробнее

The Power of Data-Oriented AttacksПодробнее

USENIX Security '20 - Exploring Connections Between Active Learning and Model ExtractionПодробнее

USENIX Security '22 - Expected Exploitability: Predicting the Development of Functional...Подробнее

D2 Elliot - Automatic exploit generation for DefenseCodeПодробнее
