USENIX Security '24 - UBA-Inf: Unlearning Activated Backdoor Attack with Influence-Driven Camouflage
USENIX Security '24 - UBA-Inf: Unlearning Activated Backdoor Attack with Influence-Driven CamouflageПодробнее

USENIX Security '24 - Neural Network Semantic Backdoor Detection and Mitigation: A Causality-Based..Подробнее

USENIX Security '24 - Shaken, not Stirred - Automated Discovery of Subtle Attacks on Protocols...Подробнее

USENIX Security '24 - You Can Obfuscate, but You Cannot Hide: CrossPoint Attacks against Network...Подробнее

USENIX Security '24 - Instruction Backdoor Attacks Against Customized LLMsПодробнее

USENIX Security '24 - On the Difficulty of Defending Contrastive Learning against Backdoor AttacksПодробнее

USENIX Security '24 - Lurking in the shadows: Unveiling Stealthy Backdoor Attacks agains...Подробнее

USENIX Security '24 - Hijacking Attacks against Neural Network by Analyzing Training DataПодробнее

USENIX Security '24 - An LLM-Assisted Easy-to-Trigger Backdoor Attack on Code Completion Models:...Подробнее

USENIX Security '24 - SoK: Neural Network Extraction Through Physical Side ChannelsПодробнее

USENIX Security '24 - FakeBehalf: Imperceptible Email Spoofing Attacks against the Delegation...Подробнее

USENIX Security '24 - Practical Data-Only Attack GenerationПодробнее

USENIX Security '24 - SoK: State of the Krawlers – Evaluating the Effectiveness of Crawling...Подробнее

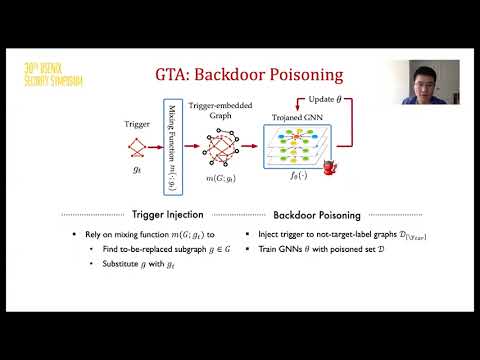
USENIX Security '21 - Graph BackdoorПодробнее
USENIX Security '24 - EaTVul: ChatGPT-based Evasion Attack Against Software Vulnerability DetectionПодробнее

USENIX Security '24 - ModelGuard: Information-Theoretic Defense Against Model Extraction AttacksПодробнее

USENIX Security '24 - Mudjacking: Patching Backdoor Vulnerabilities in Foundation ModelsПодробнее

USENIX Security '24 - A Flushing Attack on the DNS CacheПодробнее
