Using a MitM Attack for Debugging and Non-Nefarious Reasons w/ Mike Harrison

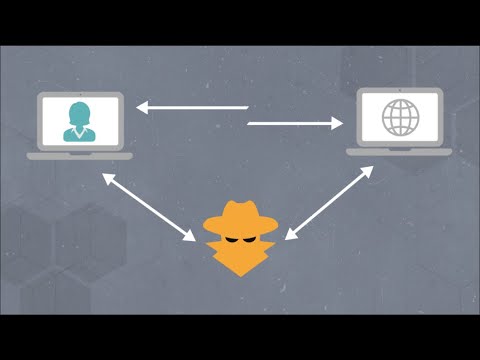
What is a Man-in-the-Middle Attack? (In About A Minute)Подробнее
MICROSOFT UNDER ATTACK!Подробнее

Understanding MitM attacksПодробнее

WiFi Wireless Security Tutorial - 15 - DNS Spoofing and MITM Attack DemoПодробнее

How to Fix CrowdStrike Issue Causing Windows Blue ScreenПодробнее

How Hackers Use Xerosploit for Advanced MiTM AttacksПодробнее

how Hackers SNiFF (capture) network traffic // MiTM attackПодробнее

MitM W - Fight TimeПодробнее

CrowdStrike's Faulty Update Sparks Global Chaos: What Went Wrong?Подробнее

Accessing Settings During Setup in ASP.NET Core / .NET 8Подробнее

Man-in-the-middle attack EXPLAINED: HOW can you to prevent MITM attackПодробнее

26 Detect MitM Attacks Part 02Подробнее

Cyber security agenda - 5 ) MITM AttackПодробнее

How Hackers Discover Your Web History!Подробнее

What is a Man-in-the-Middle Attack?Подробнее

Flipper Zero Alternative? - m5stickC plus 🤯 #shortsПодробнее

25 Detect MitM Attacks Part 01Подробнее
