Using policy as code to manage security risk in kubernetes
Implementing AI RMF with Policy-as-Code Automation - Robert Ficcaglia, Anca Sailer & Vikas AgarwalПодробнее

Using Policy as Code for Enterprise wide Authorization - DemoПодробнее

AWS re:Inforce 2023 - A deep dive into container security on AWS (APS204-S)Подробнее

Adopting Network Policies in Highly Secure Environments - Raymond de Jong, IsovalentПодробнее

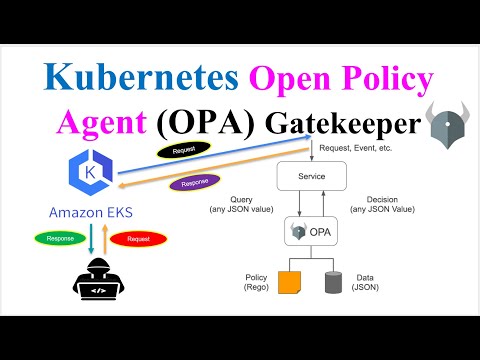
Kubernetes Security: How to Protect Your Cluster with Open Policy Agent GatekeeperПодробнее
Securing Self-Hosted GitHub Actions with Kubernetes & Actions-Runner-Controller - Natalie SomersallПодробнее

Short Demo of Advanced Cluster Security (Formerly StackRox)Подробнее

Enforcing Kubernetes Security Policies with DatreeПодробнее

Policy-Based Kubernetes Governance, Risk, and ComplianceПодробнее

Carbon Black Office Hours: Introduction to Container and Kubernetes Security (May 17, 2023)Подробнее

Getting Started with the OWASP Top 10 for KubernetesПодробнее
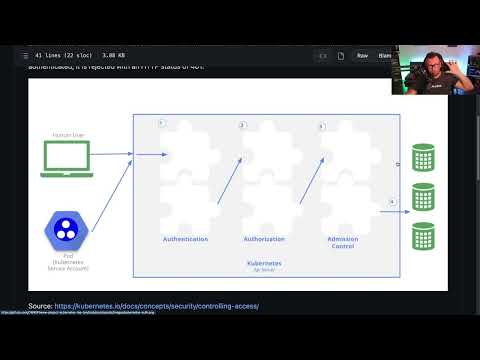
This Security Risk could NUKE your Kubernetes Node! | Alta3 BreakdownПодробнее

The Hacker’s Guide to Kubernetes Security by Patrycja WegrzynowiczПодробнее

Security in Kubernetes - Automating Your Pipeline Securely with Sonatype, Rancher Labs and NeuVectorПодробнее

Top #kubernetes Security concerns and how to address themПодробнее

BSidesBCN21 - Workshop: Rooting out security risks lurking in your kubernetes (Vasant Chinnipilli)Подробнее

GitOps on AWS: Managing Governance, Risk and Compliance for Kubernetes on EKSПодробнее

Red Hat Advanced Cluster Security - Deep dive demoПодробнее
Threat Modelling Kubernetes: A Lightspeed Introduction - Lewis Denham-Parry, Control PlaneПодробнее

Deployment-time risk management with Red Hat Advanced Cluster Security for KubernetesПодробнее
