Verifiable Credentials: How to Adopt a Zero Trust Strategy

Establishing Trust with Decentralized Identity Networks, Verifiable Credentials, and Zero TrustПодробнее

Implementing Zero Trust with Verifiable Credentials DemonstrationПодробнее
Verifiable Credentials explained with EBSIПодробнее

Verifiable Credentials: OverviewПодробнее

The Importance of Verifiable CredentialsПодробнее

Understanding and Using Verifiable CredentialsПодробнее

Verifiable Credentials and the Future of Enterprise SecurityПодробнее

Decentralized ID, verifiable credentials, zero trust represent a new paradigm for trust/verificationПодробнее

Ultimate Guide to Zero Trust for BusinessesПодробнее

Endless Possibilities with Verifiable CredentialsПодробнее

Online Identity with Verifiable Credentials and ZKPs Using High School Math - Stephen CurranПодробнее

Verifiable Credentials: Workplace CredentialsПодробнее

Transforming Cyber Defense: Zero Trust Strategies with Sean ConnellyПодробнее

Verifiable Credentials: Onboarding EmployeesПодробнее

Verifiable Credential in Actions During ID-Verification ProcessПодробнее
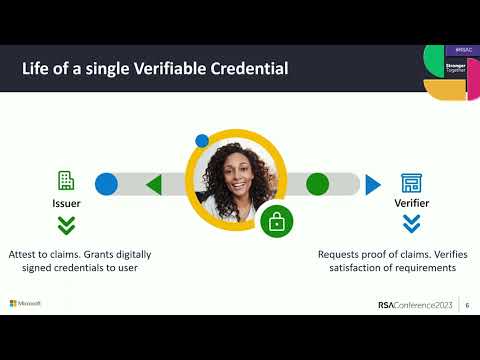
Paper-based Verifiable CredentialsПодробнее

To Net Zero with Verifiable CredentialsПодробнее

How Verifiable Credentials are already secretly being used todayПодробнее

Microsoft Zero Trust Adoption FrameworkПодробнее
