Webinar: Securing Edge Computing by Deploying Post-Quantum Cryptography

Webinar: Threats & Solutions for Application Security in the Post Quantum WorldПодробнее

Webinar: Cyber Modernization – How is Post-Quantum Cybersecurity Implemented?Подробнее

Webinar: Securing Space and Connected Ground Networks with Post-Quantum CryptographyПодробнее

Network Security Post-Quantum Full Webinar - QED-C Quantum MarketplaceПодробнее

Post-Quantum Cryptography: the Good, the Bad, and the PowerfulПодробнее

Secure the Future with Post-Quantum Cryptography on eFPGAsПодробнее

Understanding Post-Quantum Cryptography (PQC)Подробнее

Webinar: Securing Financial Transactions in a Post-Quantum WorldПодробнее

AWS re:Invent 2020: Building post-quantum cryptography for the cloudПодробнее

An AWS approach to post-quantum cryptography w/AWS Sr Principal Eng & Cryptographer Matthew CampagnaПодробнее
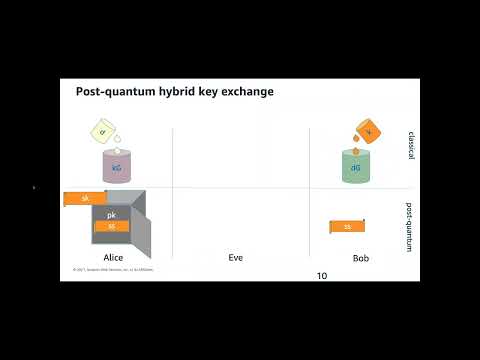
CSIAC Webinar: Quantum Security - Quantum Computing & the Threat to CybersecurityПодробнее

AWS re:Inforce 2023 - Post-quantum cryptography migration strategy for cloud services (DAP302)Подробнее

Cryptography in a (post-)quantum worldПодробнее

Protecting Our Data From Quantum Computers! | Post Quantum CryptographyПодробнее

Webinar: Quantum Cybersecurity for Any Device, Anywhere, AnytimeПодробнее
