What are Authentication vulnerabilities | OWASP Top 10 | Bug Bounty Service LLC

What are 403 vulnerabilities | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What are Developer Tools vulnerabilities | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What are Premium Feature vulnerabilities | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What are Login Form vulnerabilities | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What are Java Script vulnerabilities | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What are RESTful APIs vulnerabilities | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What are Registration Form vulnerabilities | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What are Updating Account vulnerabilities | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What are Broken Session Management vulnerabilities | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What are Password Reset vulnerabilities | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What is OAuth | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What are WebSockets | OWASP Top 10 | Bug Bounty Service LLCПодробнее

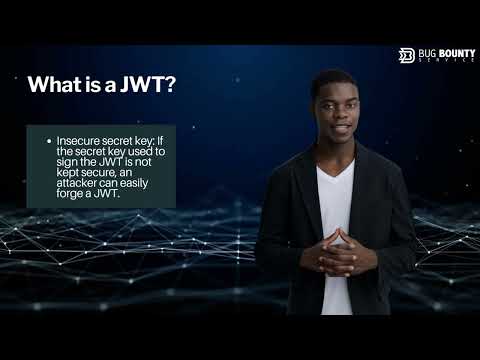
What are JWT vulnerabilities | OWASP Top 10 | Bug Bounty Service LLCПодробнее
What is a Remote Code Execution (RCE) vulnerability | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What are Access control vulnerabilities | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What are HTTP Host header attacks | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What is OSINT / Enumeration | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What are Business logic vulnerabilities | OWASP Top 10 | Bug Bounty Service LLCПодробнее

What is Insecure Deserialization | OWASP Top 10 | Bug Bounty Service LLCПодробнее
