What is Defense in Depth? - Cyber Security Course for Beginners
Defense in Depth in OT CybersecurityПодробнее

Webinar: How Defense In Depth Will Save Your Business From Cybersecurity Breaches and Data LossПодробнее

Defense in Depth: Exploring the Elements of a Layered Security ProgramПодробнее

Defense in Depth in Cybersecurity. Information Systems and Controls ISC CPA examПодробнее

Cyber Security Full Course 2024 | Cyber Security Course Training For Beginners 2024 | CyberCommunityПодробнее

CIS41A Unit 5 Lecture: Defense In Depth and Layered Security ApproachesПодробнее

The Cybersecurity Fortress: Building Defense-in-Depth with Sophos and VeeamПодробнее

Defense In Depth Access Control Concept in Cyber security - ISC2 CC #beginnersguideПодробнее

Session#02 - Building Cyber Resilience Defense in Depth and DevSecOps for Cloud SecurityПодробнее

Cyber Security Full Course | Cyber Security Training | Cyber Security Tutorial| Cybersecurity GuideПодробнее
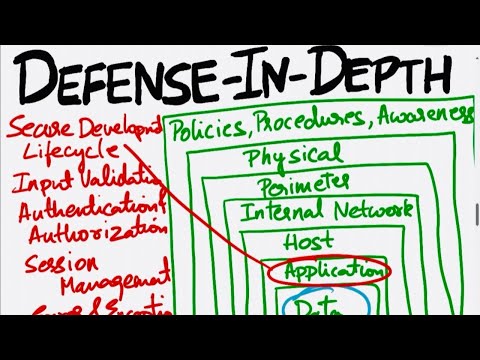
Defense in Depth | Information Security Strategy | Network Security | Cyber SecurityПодробнее

Cybersecurity Architecture: Five Principles to Follow (and One to Avoid)Подробнее

Defense In Depth - I.T. Security PoliciesПодробнее

DOF Creations & Fortinet Webinar - Defense In DepthПодробнее

Cyber Security Beginner's Course | Defense In Depth | Lecture-6 #cybercommunityПодробнее

Webinar: Cybersecurity Series, Part 1 of 3 – Defense-in-DepthПодробнее

What is Defense-in-Depth? | How to implement defense-in-depth| Layered Security| CybersecurityПодробнее
Defense In Depth - Cyber Security Risk AssessmentПодробнее

Cybersecurity Architecture: NetworksПодробнее

Cybersecurity Fundamentals - Defense in DepthПодробнее
