CNIT 129S Ch 9: Attacking Data Stores (Part 2)

Ch 9 Attacking Data Stores Part 2Подробнее

CNIT 129S: Ch 9: Attacking Data Stores (Part 2)Подробнее

Ch 9 Attacking Data Stores Part 1Подробнее

CNIT 129S: Ch 13: Attacking Users: Other Techniques (Part 2)Подробнее

CNIT 129S: Ch 13: Attacking Users: Other Techniques (Part 2 of 2)Подробнее

CNIT 129S Ch 9: Attacking Data Stores (Part 1)Подробнее

CNIT 129S: Ch 8: Access Controls & Ch 9: Data Stores (Part 1)Подробнее

CNIT 129S: Ch 7: Attacking Session Management (Part 1 of 2)Подробнее

CNIT 129S: 9: Attacking Data Stores (Part 1 of 3)Подробнее
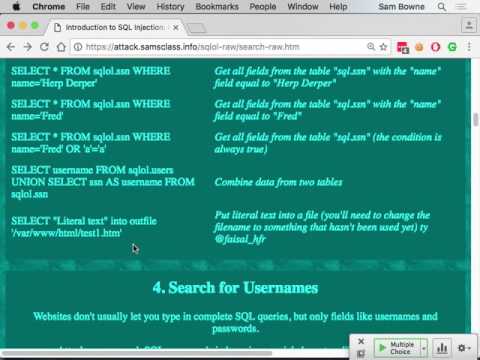
CNIT 129S: Ch 6: Attacking Authentication (Part 2 of 2)Подробнее

CNIT 129S - Ch 9: Attacking Data Stores (Part 2)Подробнее

CNIT 129S: Ch 5: Bypassing Client-Side Controls (Part 2 of 2)Подробнее

CNIT 129S - Ch 8: Attacking Access Controls & Ch 9: Attacking Data Stores (Part 1)Подробнее

CNIT 129S: 9: Attacking Data Stores (Part 3 of 3)Подробнее

CNIT 129S: 9: Attacking Data Stores (Part 2 of 3)Подробнее
