Crushing System Defenses: Certified Ethical Hackers Unleash DoS & DDoS Attacks!
Crushing System Defenses: Certified Ethical Hackers Unleash DoS & DDoS Attacks!Подробнее

Plan DOS & DDOS Attacks: An Ethical Hacker's Guide - Lec 22Подробнее

Performing DDoS Attacks (Lab) - Certified Ethical HackerПодробнее

Watch This Russian Hacker Break Into Our Computer In Minutes | CNBCПодробнее

DOS an DDOS Attack Explained 🔥🧑💻Подробнее

Denial of Service Attacks ExplainedПодробнее

DDoS Attack ExplainedПодробнее

Tate Livestream getting Attacked by HackersПодробнее

Real-Time DDoS Attack ShowcaseПодробнее

DDoS Course for Ethical Hackers & Pentesters - Theory, Setup & DEFENSE!Подробнее

WHAT IS DOS / DDOS ATTACK?|| [part-11] ||ETHICAL-HACKING BY KARTHIK||Подробнее
![WHAT IS DOS / DDOS ATTACK?|| [part-11] ||ETHICAL-HACKING BY KARTHIK||](https://img.youtube.com/vi/Vpz_NTovzd0/0.jpg)
DDoS Attack Explained #shortsПодробнее

DoS and DDoS Attacks Explained: Types and Countermeasures| Denial of Service Attack| DoS DDoS AttackПодробнее
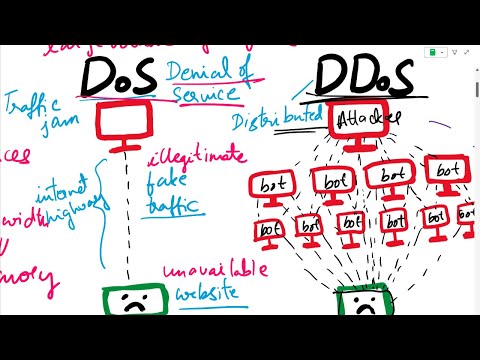
DDoS Attack Explained | How to Perform DOS Attack | Ethical Hacking and Penetration TestingПодробнее

Perform A DDoOS Atttack 💥 #hacking #subscribe #kali #linux #viral #trend #ddos #attack #freeПодробнее

DDoS Attack Impact and How to Mitigate explained by a Certified Ethical HackerПодробнее

Dos Attack || Dos/Ddos Explained + practical || (website taken Down)Подробнее

Join the July 2023 C|EH COMPETE Global Challenge: DoS/DDoS Attack | Certified Ethical HackerПодробнее

DDOS Attack Website Down #hacker #termux #hacking #cybersecurity #kalilinux #viral #ethicalhackingПодробнее

Why Kali Linux Is Used For Hacking ? | Kali Linux For Ethical Hackers #Shorts #SimplilearnПодробнее
